Governments across the world have taken a renewed interest in online safety, and age-based restrictions are often the default solution. As a parent, online safety is an issue that I care about. It is also a constant source of frustration, as tech companies and regulators often miss the mark on matters that would actually improve safety online. Worse, some of these measures actually make kids less safe.
If online safety is a topic that matters to you or if you just want to understand the issues being discussed in the news, we’re going to walk you through the good, the bad, and the ugly of age verification systems.
How do you verify age on the internet?
If you’ve been on the internet for a while, you probably know that anonymity, for better or for worse, is a core feature of online interactions. There’s a good chance the obnoxious posters in your comments section are typing from an office building in St. Petersburg while they try to make their quota, and those emails in your spam box are definitely not from a Nigerian prince.
If a platform wants to verify your age, there are a few different ways it can do it. It can collect your government ID, it can perform biometric scans, it can try to analyze your behavior on the platform, or it can employ a third-party digital ID company to handle your data.
Regardless of the method, age verification requires users to hand over much more information than just their age. This causes a lot of additional problems, not the least of which is the fact that none of these approaches is foolproof. As such, every verification method is a balancing act of the potential benefits it could provide vs. the potential harms it could cause.
The utility of age restrictions
Despite being controversial, there are some situations where most people agree that some form of age verification is a net positive. A good offline example of age verification is the MPAA movie ratings. Movie ratings were initially introduced by the Motion Picture Association of America in 1968.
While there is still plenty to criticize about the ratings system, it provides a useful shorthand for understanding the content of a film for both parents and audiences more generally. And while it prevents kids from seeing content that might be inappropriate for them, it ultimately leaves the decision with parents. If you want your 15-year-old to be able to see Oppenheimer or Deadpool in theatres, you just have to go with them. The ratings give parents information, but parents get to make their own decisions.
Another important aspect of the current movie ratings system is that it replaced the restrictive Hays Code, which had a long list of banned topics. The ratings system allowed filmmakers to create movies that wouldn’t have complied with the code’s censorship rules (such as Oppenheimer and Deadpool). Good digital solutions should also prioritize freedom of expression and respect internet users’ First Amendment rights.
An ineffective approach
While age restrictions can be a useful tool in some situations, they often fail to achieve their stated goals. For one thing, it’s impossible to break down content into age brackets that everyone agrees with. Even with broadly accepted systems like movie ratings, you can probably think of some decisions you disagree with. Did you remember that Frozen didn’t qualify for a G rating for some reason?
Age appropriateness is a very subjective measure, and trying to quantify it typically yields appropriately silly results. In 2006, for example, researchers tried to quantify the amount of violence in popular video games and concluded that the most violent games ever made included the likes of Pac-Man, Dig Dug, and Galaga. This dubious research was even presented as evidence in congressional hearings.
These are just some of the issues that come up even when you assume that all parties involved are acting in good faith. Things get a lot more complicated when people try to exploit these systems for personal gain. In the 2010s, people realized that one of the best ways to make money on YouTube was to manipulate the site’s algorithm with low-quality, and often disturbing, content directed at children. The problem was so severe that YouTube had to completely overhaul its policies toward kids’ content.
Legal issues with age verification
Age verification is a rather ineffective framework for developing online tools, but it’s a terrible idea as a legal framework. Unfortunately, there has been a recent surge of governments trying to write online age restrictions into law. Besides just not working very well, such laws in the U.S. usually come into conflict with the First Amendment.
In 2025, both Arkansas and Louisiana passed laws requiring social media companies to verify users’ ages using official documents. In both cases (Arkansas and Louisiana), the laws were found to be unconstitutional, noting that the First Amendment does not give the government the ability to choose what kinds of speech children can and cannot access.
When age verification doesn’t work
Despite these laws being struck down, political discussions about online safety often don’t get beyond blanket age restrictions. But if we want to know how such laws would work, we only have to look to Australia, which actually implemented age restrictions on social media.
Although Australian politicians touted the law as a landmark piece of legislation, it took kids less than five minutes to bypass the ban. In contrast to systems like the MPAA ratings, the Australian law does not give parents the ability to make choices about their children’s social media use. Unsurprisingly, a poll found that despite its apparent popularity, only 29 percent of parents planned to enforce the ban on their own children. Another poll found that a third of parents intended to help their children bypass the restrictions.
Creating effective age verification software has always been an elusive goal, and it’s only going to get less attainable in the future. After the messaging app Discord started using face-scanning software to enforce age restrictions, frustrated users created a free tool to bypass the system using a 3D model.
When age verification makes things worse
While age verification systems often fail to bring the benefits they promise, they can also do real harm. They are a privacy nightmare, not just to children, but to all users who give their personal data to these systems, whether willingly or not. Major data breaches are increasingly common among platforms like Discord that are collecting age verification data and third-party companies that specialize in identity verification. Requiring users to surrender personal data, especially government documents, puts them at a massive risk of identity theft. To quote Jason Kelley of the Electronic Frontier Foundation, “online age verification is incompatible with privacy.”
Even if these deeply flawed systems could be made to work as intended, the results are often still bad. The Australian social media ban, for instance, kicked millions of kids and teenagers out of their YouTube accounts, forcing them to use the site while logged out. If you’ve ever tried to use YouTube when logged out, then you probably know that the default algorithm is a cesspool of ragebait, AI slop, and misinformation. Instead of recommendations based on their interests, Australian kids had to wade through the worst of YouTube until they or their parents figured out a way to circumvent the new law.
Furthermore, many of the biggest online threats to children are in the spaces ostensibly created for children. Online predators don’t hang out on adult sites waiting for kids to come to them; they go where children already are. Spaces like Roblox, an online game platform geared toward a younger audience, have had massive issues with child abuse and exploitation.
Better ways to improve online safety
Age verification software is a clumsy, invasive, and lazy solution to online safety that infringes on constitutional rights, takes power away from parents, and distracts from more effective approaches. So what are some better ways to protect your kids online? The best tool is always to be involved with your kids, communicate with them about their online activity, and teach them digital literacy skills.
It’s also important to understand how parental controls and other content settings work on your kids’ apps and devices. There are also lots of parental control tools you can use, though many of these also rely on simple age gating by default. When looking for good parental control tools, look for those that give parents a high degree of customization and those that are applicable to the kinds of online activity your kids engage in.
On a broader, societal level, we don’t need a scan of our face and a copy of our social security card sitting on the servers of every tech company we interact with. What we do need is better content moderation and more responsive customer service so that unwanted behaviors can be blocked or prevented. We need laws that give parents more control over deciding what’s appropriate for their children and that give us more recourse against tech companies that act recklessly with our kids’ safety and privacy.
Using a VPN (virtual private network) slows down your internet connection. According to our research, you can see Wi-Fi speeds drop by as much as 77% as soon as you sign onto a VPN—but don’t fret, there’s a way to decrease the chances of your speeds dropping so drastically.
You can maintain reliable Wi-Fi speeds if you get a quality, subscription-based VPN. And you can keep your internet running smoothly as well if you keep your router updated and placed in a centralized location in your home.
Here’s a quick guide on how a VPN impacts internet bandwidth. We’ll explain why your speeds get slower with a VPN and recommend the best VPNs to maintain fast speeds.
Want to test your internet speed?
Take our internet speed test to measure how your VPN is impacting your speeds.
You can also install our mobile apps to test your speed on a smartphone!
Why does a VPN slow down your internet?
A VPN slows down your internet because it adds multiple extra steps to the process of getting data from your home internet network to your internet provider and back.
VPNs work by letting you sign on to a separate server—usually located in a different state or foreign country. This creates a virtual tunnel that masks your online activity, IP address, and location, keeping you safe from hacking and online surveillance and giving you access to websites that you might not be able to visit otherwise (like foreign versions of Netflix).
But encryption takes up bandwidth, routing a VPN through a foreign server increases latency (especially if it’s a server located in a distant state or country). A VPN’s own server bandwidth and efficiency can also impact your speed. If a VPN server is crowded with other users, it can lead to slower speeds and a less reliable connection.
On the flip side, a VPN can also combat speed throttling from an ISP, as it masks the kind of data you use. So if your provider, say, caps video streaming at 5 Mbps, using a VPN could potentially improve your speed. Let’s take a look at the best VPNs you can get to maintain fast internet speeds.
Best VPNs for fast internet speeds
| Service | Starting price (monthly) | # of servers | Max devices per subscription |
|---|---|---|---|
| NordVPN | $12.99/mo. | 7,900+ | 10 |
| ExpressVPN | $12.99/mo. | 3,000+ | 8 |
| Surfshark | $15.45/mo. | 3,200+ | Unlimited |
| Private Internet | $11.99/mo. | 10,000+ | Unlimited |
| Hotspot Shield | $12.99/mo. | 1,800+ | 10 |
| CyberGhost | $12.99/mo. | 9,700+ | 7 |
| Hide.me | Free or $9.99/mo. for paid version | 2,600+ | 1 (10 for paid service) |
You can get a massive discount from most of these VPNs by signing up for a longer subscription. Most range from 6 months all the way up to 26 months. If you plan on using your VPN long-term, we highly recommend going with a longer subscription that can help you save on the monthly cost.
NordVPN, ExpressVPN, and Surfshark consistently rank as the fastest VPNs among reviewers and experts—and they’re generally considered the best VPNs for privacy and other features, too. All three use efficient, up-to-date encryption protocols and have enough servers so you’re less likely to experience major network congestion when you sign on.
Private Internet Access, Hotspot Shield, and CyberGhost are also well-known VPNs and have performed excellently in many speed tests. Private Internet Access also boasts the most servers of any VPN in the world, giving you more options to choose from. Hide.me isn’t as fast, but it’s a great free VPN service that doesn’t eat as much bandwidth as most free VPNs.
Find fast internet providers in your area
Enter your zip code below to find all internet plans and providers available to you.
Want to see how a VPN impacts your speed? Take a speed test
Take our speed test to see if your VPN is slowing down your internet.
Even the best VPN speeds can fluctuate daily. Your internet speed can also easily be impacted by a range of other factors, including your internet provider, the connection type, your plan, and the router you’re using. But a speed test gives you a ballpark estimate of how different VPNs impact your bandwidth.
Here’s a quick rundown on how to do it.
How to test VPN speed
Step one: Run a speed test with your VPN disabled. Write down the results.
Step two: Turn on the VPN and run the test again. Write down these results as well.
Step three: Compare the two speeds to see how they are different.
Step four: Repeat the process a few times throughout the day to see how the numbers differ.
How can you make a VPN faster (or at least not as slow)?
It’s hard to predict just how much a VPN may slow your internet speed because a lot of factors play into the speeds you’re getting. But there are a few things you can do to make sure you’re getting the most out of your VPN, speed-wise.
Avoid free VPNs
Free VPNs might work if you’re on a budget, but they typically don’t perform as well as subscription-based VPNs. They have fewer servers, so you have to share a single server with more users, and some are also loaded with malware that drains your bandwidth or even hijacks it for nefarious purposes. Also, some lesser VPNs collect your user data and sell it to make money, which is another good reason to avoid them.
To ensure the best speeds—not to mention the best security and other features—stick to a well-vetted VPN that costs a monthly or annual subscription.
Switch your VPN server location
The best VPNs host servers all over the world. Some servers may perform better than others, depending on where they’re located and how many users are on each one. Try picking a server close to you to reduce the amount of time it takes to route your data to and from the VPN server.
Troubleshoot your internet connection
There are lots of ways to improve your internet connection. In addition to these VPN fixes, you can:
- Get a router with Wi-Fi 5 or Wi-Fi 6 standards
- Move your router to a centralized location in your home
- Plug your computer directly into your modem/router with Ethernet
- Remove unwanted users from your Wi-Fi network
- Upgrade to a faster internet plan
Take a look at our guide to faster Wi-Fi for more ideas.
Use the WireGuard protocol
Although OpenVPN is the most common and best-respected VPN protocol in use today, a newer protocol called WireGuard has been drawing positive attention since it launched in early 2021. Speed tests show it to be faster and more efficient than OpenVPN—although the latter still remains stronger for privacy.1, 2
Most top-rated VPNs allow you to switch between different protocols, and NordVPN specifically supports WireGuard. You can switch between protocols on your VPN by going to the settings menu. Also, you can adjust the protocol settings to make your speeds faster.
Get a better VPN
Of course, if you’re experiencing consistent speed issues on your VPN, you can always try a new VPN to see if it fares better. NordVPN, ExpressVPN, and Surfshark are often the top-rated VPNs, but there are plenty of others worth trying. See our guide to the best VPNs for recommendations.
Your internet plan might be what's slowing down your speeds
Enter your zip code below to check out the fastest internet plans available in your area.
Sources
- JP Jones, TopVPN.com, “Wireguard vs. OpenVPN,” March 11, 2022. Accessed April 14, 2022.
- Sven Taylor, RestorePrivacy, “Wireguard VPN: Secure and Fast, but Bad for Privacy?” January 10, 2022. Accessed April 14, 2022.
More about VPNs and internet speed
Internet issues are just a way of life. There’s always something disrupting your dancing cat videos. Network troubles on your provider’s side. Storms blowing down lines. The speed woes of a tired old router. Kids downloading super-sized game updates. Something.
But what if every device you own loads the same website no matter what you type into the address bar? Or, even worse, you sit at your computer, utterly speechless, as a “ghost” seizes your mouse and opens your bank account?
Not fun.
Those two scenarios alone are good signs of a hacked router. But don’t worry: I’ll clue you in on how to recognize a hacked router, how to fix it, and how to make sure it never happens again.
Are you sure you've been hacked?
You may not have a hacked router but a slow internet plan. Enter your zip code below to find a faster plan in your area.
Signs that someone hacked your router
There are many signs of a possible router hack that can throw up a red flag. Some are general and could apply to other router-related issues. Others are a sure sign that someone else now controls your network.
Sign #1—You can’t log in to your router
First, let’s be clear that your inability to sign in to your router or gateway doesn’t always mean you’ve been hacked. There have been plenty of times when I returned to a router I previously tested, and it (rather rudely) denied me access to the settings. This is not an uncommon problem. It usually means you’re entering the wrong password, you misspelled the password, or something on the router side is corrupt. Case closed.
With that said, there’s also the slim possibility that someone hacked your router. The attacker may have figured out the credentials, logged in, and changed the password to lock you out. After that, the attacker has free reign to change additional settings and make your life miserable.
But why did the attacker target you? Perhaps you clicked on a clever email or message link, and now the hacker has full control of your home network. Hackers also probe the internet for vulnerable routers they can use to create botnets, steal your bank login info, and so on.
Welcome to the modern-day World Wide Web.
So, whether you’re hacked or just having password issues, the only remedy is to reset your router to its factory defaults.
Take immediate action!
Follow our instructions on how to reset your router.
Sign #2—All internet browsers lead to the same site
Browser hijacking is a sure sign that you have a hacked router or gateway.
In this case, a hacker logged in to your router and changed its Domain Name System (DNS) settings—the system that matches numeric IP addresses with the alphanumeric ones we see and easily remember, like google.com.
By doing so, the hacker can redirect all your internet traffic to a malicious DNS server. This server will lock you to specific websites that can steal your information and install malicious software on every internet-connected device you own.
Take immediate action!
Log in to your router and change the DNS settings and password. If you can’t log in, reset your router. You should also scan every device with antivirus software to make sure there’s nothing on your devices that’s hijacking your browser.
Sign #3—There’s strange software on more than one device
If you see new, unfamiliar software on more than one device—especially if you didn’t download it intentionally—there’s a good chance someone hacked your router and remotely installed malware onto your devices.
Strange, uninvited software includes browser toolbars, fake antivirus clients, and other programs that will generate random popups on your screen or within a browser.
If you have multiple computers, this uninvited software may be on all of them. Malware can replicate on a single device and spread across wired and wireless connections, similar to how a virus spreads from person to person.
Take immediate action!
Log in to your router and change the password. If you can’t log in, reset your router. Afterward, make sure your router has the latest firmware. Be sure to uninstall the strange software from your device(s) and run an antivirus client.
Sign #4—You receive a ransomware message
Ransomware messages can be a sign that you have a hacked router. These attackers can seize control of the router and demand money in return for its release. The message may appear in the form of an email, instant message, text, or a popup generated by uninvited software installed on your device.
But also remain skeptical. Ransomware messages don’t always mean you’ve been hacked. Some are designed to instill fear and convince you of a hack that never happened. But if you see popup threats on your screen or your mouse suddenly opens your bank account, then yes, you’re under attack.
Take immediate action!
Don’t pay a dime, and follow my instructions on how to reset your router. Be sure to create a unique password that hackers can’t guess.
Sign #5—You see unrecognized devices on your network
You can use the router’s web interface or mobile app to see a list of devices connected to your home or office network. For example, the Linksys Smart Wi-Fi interface provides a network map—just click on a device to see its assigned address.
When you look at the map, all local devices have a derivative of the router’s private IP address. If your router’s address is 192.168.1.1, for example, then all device addresses should start with the first three numbers (192.168.1).
However, a device remotely accessing your router won’t have an address that matches the first three numbers of your router’s private address.
Take immediate action!
Kick the unknown device(s) off your network and change the password. Disable remote access if you never use it.
Sign #6—You can’t control your device
If you sit in front of your computer and watch an uninvited, unseen guest move the mouse and access your banking information, you definitely have a hacked router.
In this scenario, the hacker has remote access to your device and can open any file or online account using the passwords you store in the operating system or browser.
Take immediate action!
Unplug your devices and disconnect your router from your modem. After that, follow my instructions on how to reset your router. Change your passwords, too.
Sign #7—Your internet speeds are slower than snails
Slow internet speeds aren’t uncommon. There may be issues with your provider, too many devices downloading at one time, and so on. But if you experience extremely slow speeds along with other symptoms on this list, chances are you have a hacked router.
Your speeds could be slow because the hacker seized your full bandwidth for the following:
- Botnet activity
- Distributing malware to other networks
- Remote connections to your devices
- Cryptojacking
- General internet piggybacking
Take immediate action!
First, use our tips on how to speed up your internet to see if the problem is just a connection issue. If you think that someone hacked your router, try to change the password. If you can’t, follow my instructions on how to reset your router.
How to fix a hacked router or gateway
You can easily and quickly fix a hacked router. There’s no need to throw it out the window and purchase a new one.
Step 1: Disconnect the router or gateway
If you have a standalone router, disconnect the Ethernet cord to avoid communicating with the modem. If you have a gateway, disconnect the internet connection instead.
In both cases, disconnect all other wired and wireless devices.
Step 2: Power cycle your router or wireless gateway
In some router hacking cases, a simple power cycle (reboot) works as a quick fix. This method clears the memory of any malicious code and refreshes your public IP address. Just pull the plug, wait 30 seconds, and then plug the cord back into the outlet.
In other cases, you may need to reset your router to its factory settings. A power cycle cannot remove severe infections like VPNFilter.
Step 3: Change the password
Once you power cycle the router, log in and change the password. You can use one of the best password managers to create one and retrieve it from your account when needed.
Actually, I suggest you create a passphrase instead of a password. It’s a long string of unrelated words filled with symbols and numbers. Make it something you can remember but isn’t easily guessed.
Do the same with your Wi-Fi network, too.
Immediate action: Read my guide on how to change your Wi-Fi network name and password.
Step 4: Update the firmware
Set your router to update its firmware automatically if it’s not already. And if your router doesn’t give you the option to update automatically, set yourself a reminder to check every month or so.
But carry out either method with caution, as faulty firmware can render your router useless. Check the manufacturer’s notes to make sure the latest firmware is stable. You shouldn’t have any issues with new firmware, but it doesn’t hurt to be cautious and proactive. Routers aren’t cheap.
Immediate action: Read my guide on how to update the firmware on routers from several popular brands.
Step 5: Reset your router
if an infection persists or you can’t log in, then a router reset is your only solution (outside buying a new one). A reset restores the factory default settings, clearing out any possible malware. You’re essentially rebuilding your home network and creating new passwords for the router login and Wi-Fi.
For more information, consult my guide on how to reset a router from ASUS, Linksys, NETGEAR, and more.
How to prevent a router hack
Use the following suggestion to safeguard your devices and sensitive data against hackers.
Stay on top of firmware updates
Your router is a miniature computer with a processor, system memory, and storage that houses the operating system (firmware). Unfortunately, firmware is never bulletproof, as there can be bugs in the code and security holes. Attackers will utilize these unpatched flaws and access your router with ease.
Manufacturers distribute firmware updates regularly to squash these bugs and patch vulnerabilities. Generally, we suggest you enable automatic firmware updates if the feature isn’t toggled on already and you never manually install new firmware. Log in to your router and toggle on automatic updates if they are not already.
However, be aware that things can happen. Bad firmware uploaded to a manufacturer’s distribution server can brick your router. Malware-infected firmware distributed to a router can lock you out. Auto-updates are convenient, but there’s a rare chance the update can go awry and leave you with a $300 paperweight. For this reason, some manufacturers don’t support auto-updates.
Read my guide on how to update the firmware on routers from several popular brands.
Use a secure password
Every router I’ve tested forces you to create an administration password during setup. There’s usually no “default” password that hackers can pass around. Some routers even require you to create two security questions for accessing the router when the admin password doesn’t work (corrupt, forgotten, etc.). The password normally requires a mix of upper- and lower-case letters, numbers, and symbols.
Likewise, every router I’ve tested ships with a unique passphrase for Wi-Fi printed on a label. You’re prompted to change it as you move further into the setup, but it’s not mandatory like the administration one.
Some routers require a cloud account prior to starting the setup process, like mesh networking systems. That means you must create a username and password to use the service and router.
Overall, never use an easily guessed password with your router or Wi-Fi network—even if it’s full of upper- and lower-case letters, numbers, and symbols. These include names of pets, children, other family members, and anything that links to your interests. Believe it or not, the two most used passwords are still password and 123456. Like, really?
So, what’s the big deal? Why can’t we use easily remembered passwords? Because a hacker can use free online tools to carry out a brute-force attack—a trial-and-error method that continuously enters every possible password until one works. Hackers can also use a library attack, which uses words pulled from a dictionary. These attacks can quickly crack an easy eight-character alphanumeric password.
The bottom line here is use a passphrase instead of a password. It’s a string of unrelated words with symbols and numbers that’s harder to crack than any password you create.
Schedule routine reboots
A monthly reboot is good for the router, as it can clear the system memory and refresh all connections.
Additionally, your internet provider assigns a public IP address to your router. It usually refreshes every 14 days anyway (unless you pay for a permanent “static” address), but a reboot gives you an extra refresh if hackers obtained one of your previous addresses.
Disable remote access
Remote access is a feature for changing the router’s settings when you’re off the network, like from a hotel room. Most routers now have two methods, but the one you should be concerned about lies within the web interface. It’s an easy entry point for attackers, especially if you use a weak password.
Based on the routers I’ve tested, this feature is disabled by default in favor of cloud-based access through mobile apps. Still, you should check to see if it’s disabled, and if not, turn it off immediately. Only use this version of remote access if the app doesn’t have the settings you need to change off-network—and only do so sparingly.
Be sure to use strong passwords or passphrases when you set up a cloud account (if you choose not to use the complex ones supplied by Android and Apple devices). Also, enable biometrics so you’re not manually entering login credentials out in public.
Disable WPS
Wi-Fi Protected Setup (WPS) has good intentions. It allows users to connect their devices to a wireless network without a password. Simply press the WPS button on the router, or enter an eight-digit PIN provided by the router.
But the convenience has a major drawback. Hackers can use a brute-force attack to figure out the PIN in 4 to 10 hours—they don’t need access to the physical button. You can easily disable WPS through the router’s backend and instead use our guide on how to share your Wi-Fi network’s password to any device.
If you have a Linksys router, for example, you can disable WPS by doing the following:
Step 1: Select Wi-Fi Settings displayed under Router Settings.
Step 2: Click on the Wi-Fi Protected Setup tab.
Step 3: Click the toggle so that it reads OFF.
Step 4: Click on the Apply button. You must click this button so that WPS and its related PIN are completely disabled—clicking on the toggle without applying the change isn’t enough.
Change the network name
The Service Set Identifier (SSID) is your wireless network’s name. All routers broadcast the manufacturer’s name by default, like Linksys_330324GHz or NETGEAR_Wi-Fi. Anyone within range can see this name, know who built your router, and search the internet for the default login credentials if they’re available.
However, the router prompts you to rename the wireless network during the setup process for that very reason. If you ignored the router’s request, now is a good time to return to the settings and change the network name. Use whatever you want, just don’t advertise anything that can help attackers infiltrate your home network.
If you have band steering turned on, you’ll only need to change one SSID. If band steering is turned off, you’ll have at least two Wi-Fi connections to rename. I normally add a “2” or “5” suffix to distinguish between the different bands, like “clearlink2” and “clearlink5” as seen in my router reviews. At home, I use different NSFW names to annoy my neighbors.
Finally, network names can be up to 32 characters long.

Want to keep hackers off your network?
We suggest one of the best routers for security.
How to protect your devices from hacks
There’s more to protecting your network against hackers than securing your router. You need safeguards in place to protect your devices and personal data, too, should an attacker take control of your router.
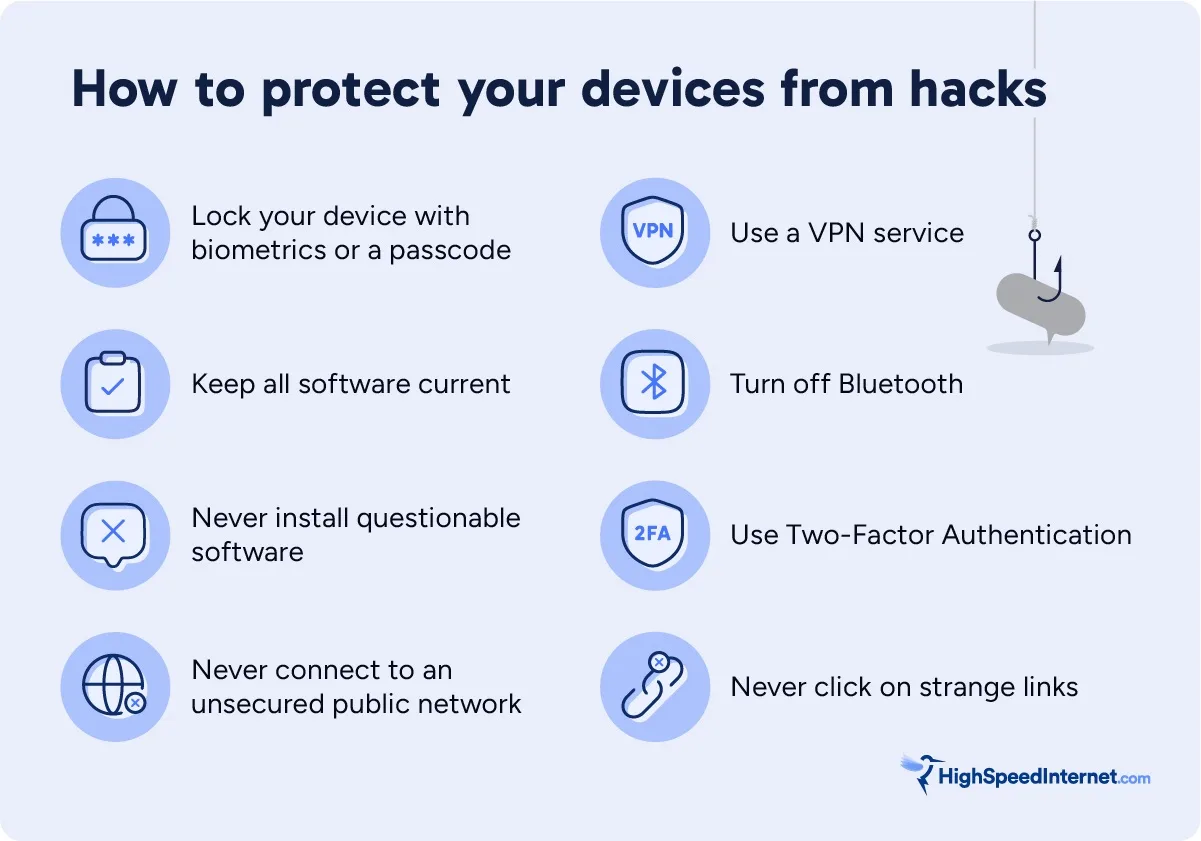
Computers and mobile devices
Lock your device with biometrics or a passcode
Use facial recognition and fingerprint scanning to lock your devices and accounts in addition to using the main login password. Passcodes and patterns are better than passwords, too, but you run the risk of someone guessing them correctly by viewing the smudges on your screen.
Keep all software current
Device manufacturers like Apple and Lenovo release system updates to squash bugs in the code, optimize performance, and fill security holes. Software developers do the same, so be sure every platform, desktop software, and app you use is current.
Never install questionable software
If the desktop software or app—or even the website that hosts it—looks shady, then don’t install it. Always get your apps and software from verified sources versus back-alley repositories lurking in the dark corners of the internet.
Never connect to an unsecured public network
An unsecured public network means the Wi-Fi connection doesn’t use any security. The data you send and receive from an unsecure Wi-Fi access point isn’t protected from eavesdropping hackers eager to steal your info.
Use a VPN service
Many modern routers now support OpenVPN, a free VPN service you can use to hide your online activity. All you need is to enable the server on your router and install the client software on your devices. We also provide a list of the best VPN services if your router doesn’t include a VPN server.
Turn off Bluetooth
Bluetooth is another form of wireless communication. Device manufacturers like Apple say to keep it turned on “for the best experience” but the Federal Communications Commission suggests you turn it off when not in use, as hackers can access your device by spoofing other Bluetooth devices you use. If you must enable Bluetooth, use it in “hidden” mode.
Use Two-Factor Authentication
Always, always enable two-factor authentication on every account you use. It’s a pain, we know, but that added layer of security keeps hackers at bay should they somehow get your login credentials. For example, Microsoft Authenticator requires you to verify a login request in the mobile app before you can log in to your Microsoft Account on any device, including the Xbox consoles.
Never click or tap on strange links
Malware you unintentionally download to your computer or mobile device could lead the way to a hacked router. Here are several ways you can get unwanted malware:
- Click on a link in a phishing email or chat message
- Connect an infected flash drive
- Access a malicious website
- View infected ads
Computers only
Keep your antivirus current
Apple macOS doesn’t include built-in antivirus because hackers rarely ever target the platform. Microsoft Windows is a different story, however, and includes antivirus protection for free. Be sure to keep it and any third-party antivirus software you have installed on Mac or Windows up-to-date, so you stay protected against the latest threats.
Never ever disable your firewall
All computing devices have a firewall that monitors your network traffic flow but you can disable it on Mac and Windows. This is a bad idea, as you remove all restrictions and open the door for hackers to slip in and infiltrate your device. I provide instructions on how to re-enable your firewall on Windows and Mac if, for some reason, it’s disabled.
PlayStation has been around since 1994, and those of us who grew up with the brand probably already know how to set the parental controls for our kids. But what if you’re not a gamer and you just purchased a PlayStation 5 or PlayStation 5 Pro for Christmas?
Don’t fret. I’ll show you how to create accounts directly on the PlayStation 5 console, and then go over some additional settings in the web portal. I’ll also show you how to use the new PlayStation Family app, which makes family management super easy!
Before we begin
You don’t need a PlayStation Network (PSN) account to play physical and single-player games offline. However, you need an account for everything else: console and game updates, access to PlayStation Store purchases, and all the online components. Accounts are also required to use the family controls.
You can create accounts using a web browser or a PlayStation console. We’ll use the latter since it’s the easiest of the two.
Note that a PSN account can be used with PlayStation-branded consoles and apps like the PlayStation App and PS Remote Play.
Do you have the best internet for the PlayStation Network?
Make sure you have plenty of bandwidth to play your PlayStation games online, plus allow other devices to stream 4K content uninterrupted. Enter your zip code to find the best connection!
How to create PlayStation Network accounts using a console
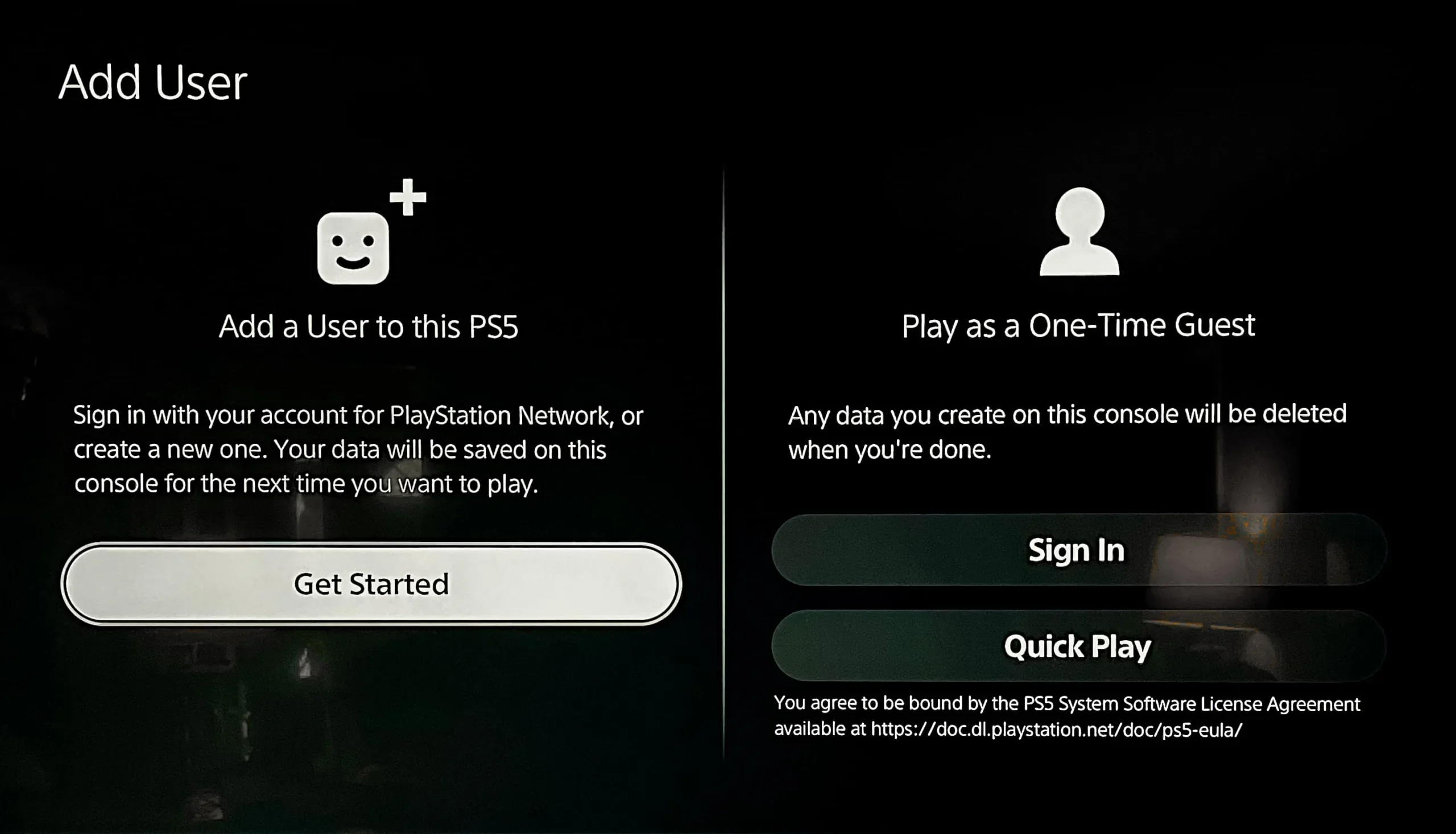
Let’s assume you purchased a PlayStation 5 for the family to use or gifted it to your child. You first need to create a parent/guardian account, and then make an account for each child.
Create a parent/guardian account
Step 1: Select Add User on the console, followed by Get Started.
Step 2: Agree to Sony’s licensing agreement to proceed.
Step 3: Select Create an Account.
Step 4: Enter your date of birth and then select Next.
Step 5: Select your country or region and preferred language, and then select Next.
Step 6: Enter a valid email address, create a password, re-enter the password, and then select Next.
Step 7: Select an avatar image for your account ,and then select Next.
Step 8: Create your Online ID (gamertag), and then select Next.
Step 9: Choose a privacy profile and then select Review and Customize or Apply.
Step 10: You received an email to verify your email address. On the screen, select Already Verified or Do This Later. You must verify your email account to use your new Sony Account.
Step 11: Select OK to finish.
Step 12: Set your two-step verification by selecting Text Message or Authenticator App. Select Do This Later to set this up at another time.
Step 13: Add a mobile number or select Do This Later.
Step 14: Select OK to complete the setup.
Now that you have created an account, you can set your avatar, edit your Online ID (for a fee), link streaming services, set your payment method, and so on. But since we’re here to set up parental controls, we’ll move on to creating a child’s account.
Create a child’s managed account
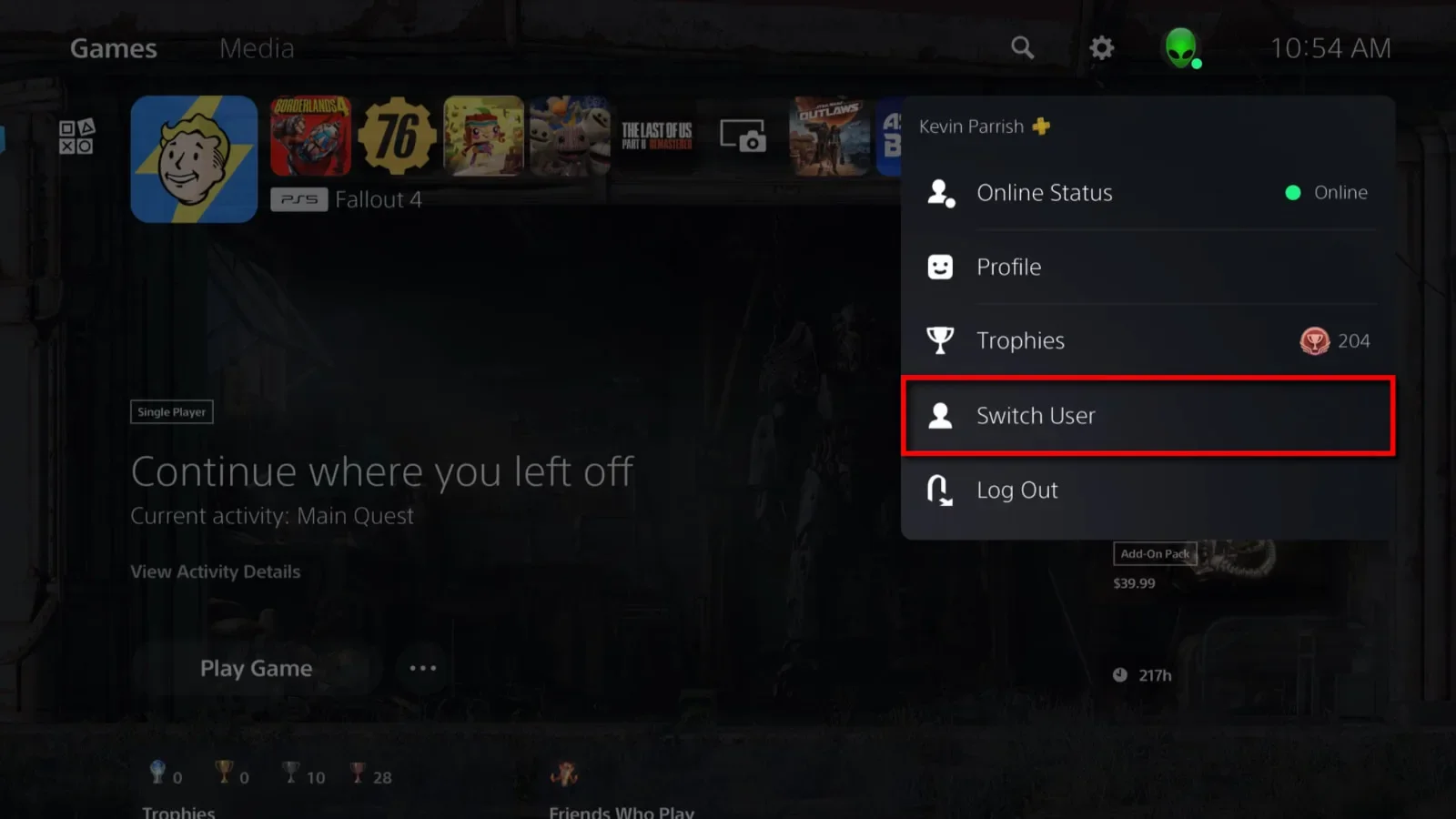
Step 1: Select your avatar on the home screen.
Step 2: Select Switch User from the drop-down menu.
Step 3: Select Add User, followed by Get Started.
Step 4: Agree to Sony’s licensing agreement to proceed.
Step 5: Select Create an Account.
Step 6: Enter your child’s date of birth and then select Next.
Step 7: Select Continue.
Step 8: Select the parent/guardian account and sign in.
Step 9: Confirm the child’s date of birth.
Step 10: Enter the child’s email address, create a password, re-enter the password, and then select Next.
Step 11: Choose a Privacy Profile and then select Review and Customize or Apply.
Here’s more on each Privacy Profile:
- Social and Open: Any player can see the child’s profile information, make friend requests, and send messages.
- Team Player: Any player can see most of the child’s profile. They must be friends of friends to chat.
- Friend Focused: Only friends can see your child’s profile and chat.
- Solo and Focused: No player can see your child’s profile or chat.
I cover the privacy settings later in the web browser portion.
Step 12: Set the Restriction Level.
Here are the restriction levels:
- Late Teens or Older
- Early Teens
- Child
- No Restrictions
Each restriction level contains customized settings. However, you can select Customize to edit the following:
- PS5 games and apps: Don’t Restrict, Age 21 or Older, Manually Set the Age
- PS4 and PS3 games and apps: Don’t Restrict, Manually Set the Age
- Blu-ray Disc: Don’t Restrict, Manually Set the Age
- DVD: Don’t Restrict, Manually Set the Age
- Country or Region (for Blu-ray Discs and DVDs): Manually Choose your Location
- Use of PlayStation VR2 and VR: Don’t Restrict, Restrict
- Web Browsing: Don’t Restrict, Restrict
- Communication and User-Generated Content: Don’t Restrict, Restrict
- Age Filtering for Online Content: Don’t Restrict, Restrict
- Monthly Spending Limit: Manually Set a Value
Step 13: Select Confirm to finish.
Step 14: Select Set Up Now to manage the child’s playtime, or select Do This Later.
Step 15: Your child received an email to verify their email address. On the screen, select Already Verified or Do This Later. You must verify the email account to use your child’s new Sony Account.
Step 16: Select OK to finish.
Do you have the best Wi-Fi for your PlayStation console?
I’ve tested a boatload of standalone routers and mesh systems. If your Wi-Fi isn’t up to snuff, check out my guide to the best gaming routers or the fastest routers I’ve tested.
How to tweak the parental controls using a console
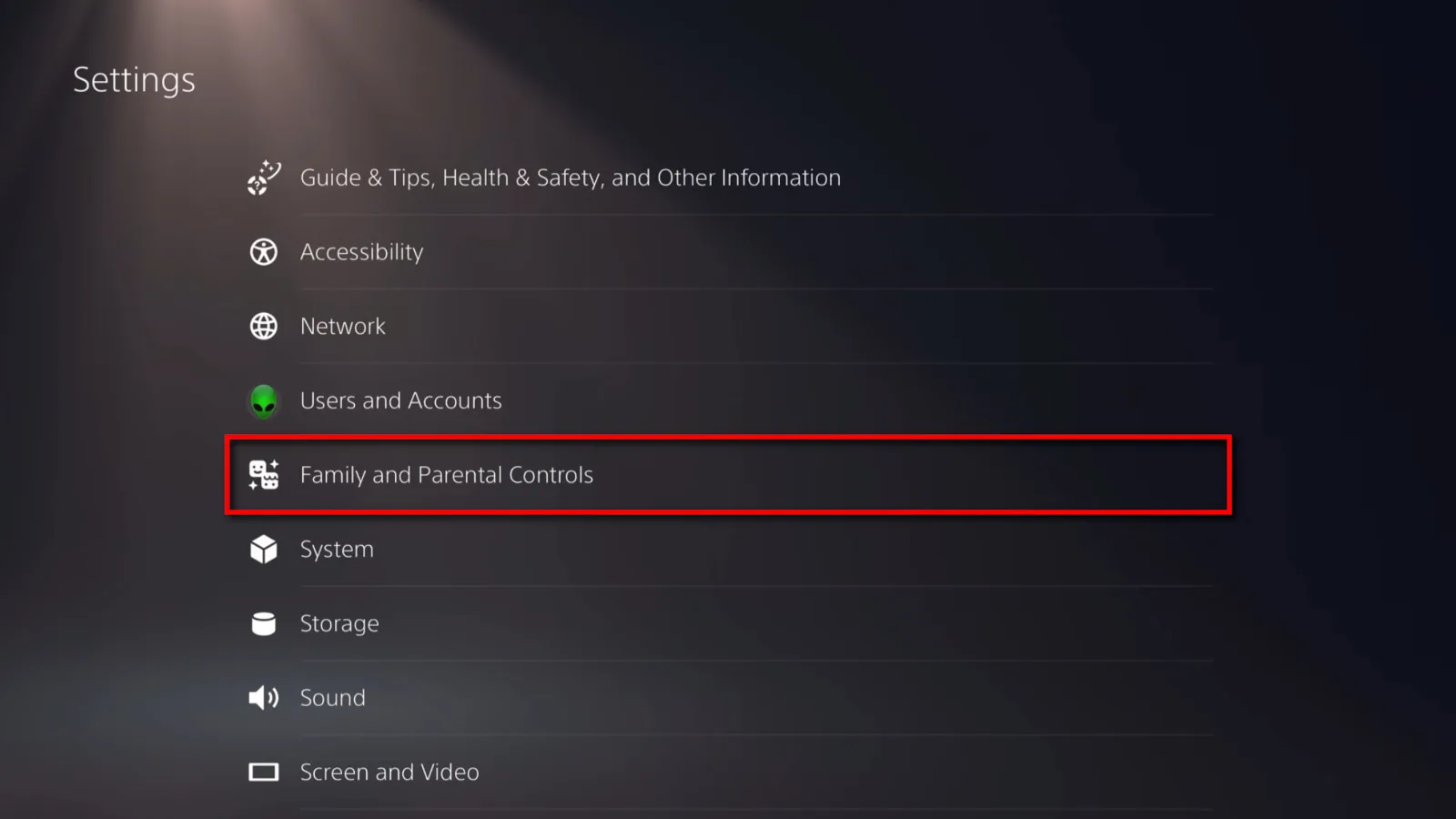
Now that the child’s account is set up, you can tweak the settings.
Step 1: On the Home screen, select the Settings gear icon located at the top.
Step 2: Select Family and Parental Controls.
Step 3: Scroll down and select your child’s account.
Step 4: Sign in to your account.
Here’s an overview of what you can set
Playtime Settings
Here you can decide when the child can play and for how long.
- Restrict Playtime: Enable/disable
- When Playtime Ends: Notify Only, Log Out of PS5/PS4/PS3
- Duration and Playtime Hours: Same Every Day, By Days of the Week
- Every Day (if chosen): Playtime Duration, Playable hours (start and end times)
- By Days of the Week (if chosen): Set hours and time
Time Zone
You already set this, but you can readjust if necessary
Parental Controls
Here, you reset the restriction level if needed.
Allowed Games
- Gameplay: You’ll see requests to play games restricted by the age level you set.
- Communication: You’ll see requests to use communication features in a specific game if the Communication and User-Generated Content setting is set to Strict.
Services and Apps
- Linked Services: See a list of services your child can link to their Sony Account.
- Authorized Apps: See a list of apps that can access your child’s information.
Privacy Settings
You’re prompted to use a QR code to change the settings in a web browser.
Family Member Information
Shows the child’s email address and Online ID
Reset Password
Enter a new password and re-enter it again to confirm.
Other Family and Parental Controls settings
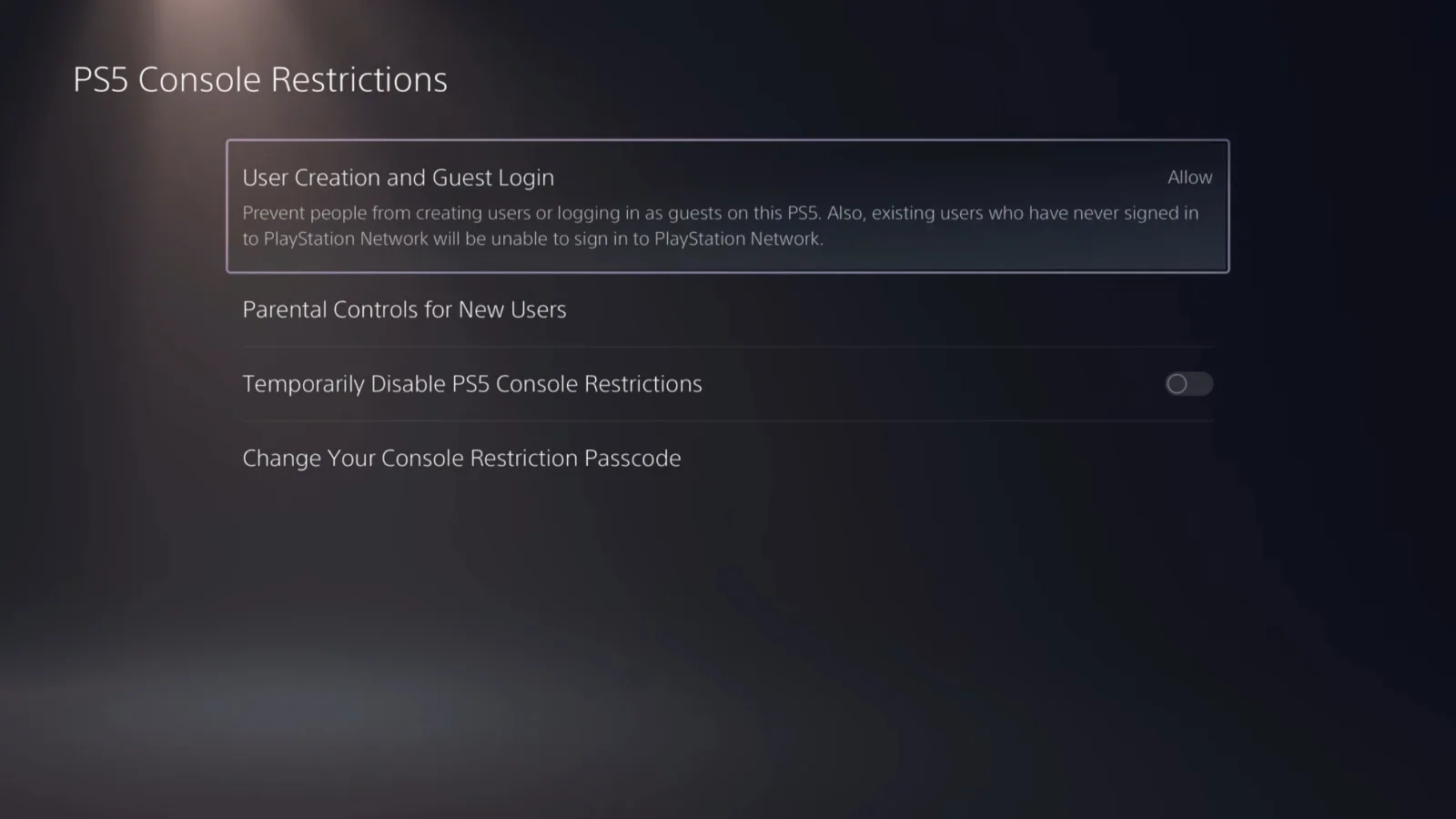
In addition to setting up parental controls for your child, there are two other parts of the Family and Parental Controls section you can adjust. Take a look:
PS5 Console Restrictions
- User Creation and Guest Login: Allow, Don’t Allow
- Parental Controls for New Users: It’s similar to the restrictions portion when setting up a child’s account: Set the age level for PS5 games and apps, restrict web browsing, and so on.
- Temporarily Disable PS5 Console Restrictions: Let all Sony Account owners use any game, app, or device without parental control restrictions (on/off).
- Change Your Console Restriction Passcode: The default is 0000, so change it if you don’t want kids disabling parental controls (and they will lol).
Family Management
Select a family member or Add Family Member. If you access an existing account, you’ll see the same parental control settings you already customized, like Playtime, Parental Controls, Allowed Games, and so on.
Next, we’ll show you how to adjust the privacy settings in a web browser.
How to manage the family using a web browser
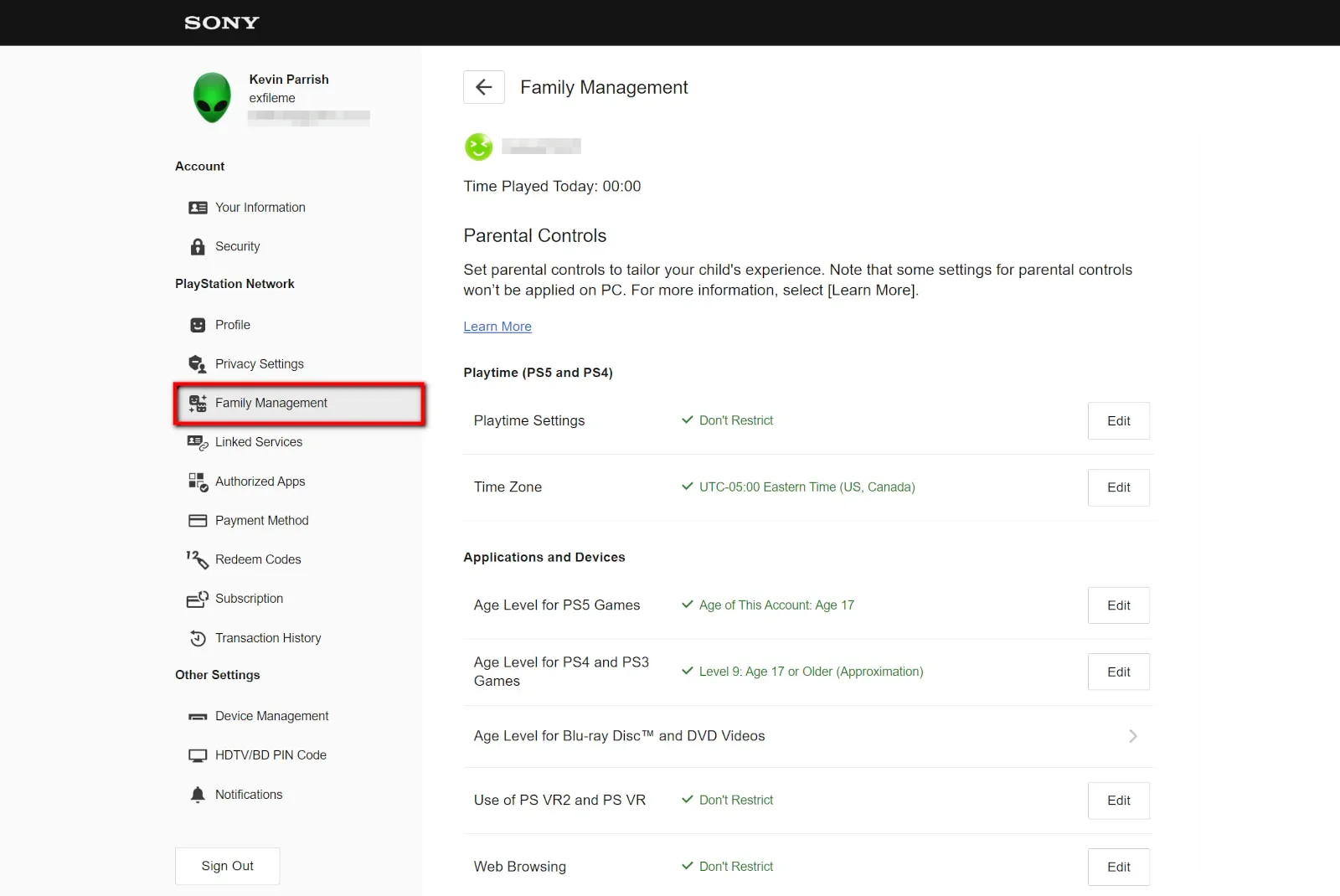
At first, I wrote instructions on how to make accounts using a web browser, but doing so on the console seemed easier. You end up accessing your accounts in a browser anyway, but at least most of the work is already done. We’ll assume you’ve already created the parent/guardian account at the very least.
Step 1: Go to playstation.com and select the Sign In button located in the top right.
Step 2: Enter your login credentials.
Step 3: Select your account avatar in the top right corner.
Step 4: Select Account Settings in the drop-down menu.
Here, you’ll see details specific to your account, like linked services, authorized apps, your payment method, and so on.
Step 5: Select Family Management on the left.
Step 6: Select the child’s account you want to modify, or select Add Family Member if you have other accounts you need to add.
You’ll see everything you’ve already set: Playtime, apps and devices, web browsing restrictions, and so on.
However, the web browser is where you’re directed when you want to set the Privacy Settings. Scroll down on the child’s account and select Edit to modify the settings. You have an option to allow the child to set their privacy settings or allow the parent/guardian.
Here’s a list of what you and your child can change.
Settings applied to PS5, PS4, and PC
- Who can see your child’s games and trophies: No One, Friends Only, Friends of Friends, Anyone
- Who can see your child’s online status and what they’re currently playing: Friends Only, Friends of Friends, Anyone
- Who can ask to be your child’s friend: Anyone, Friends of Friends, No One
- Who can interact with your child through parties, games, and messages: Anyone, No One, Friends Only
Settings applied to PS5 and PS4
- Who can see your child’s friends: No One, Friends Only, Friends of Friends, Anyone
- Your child’s personalized content: Personalized Purchase Recommendations, Personalized Advertising, Personalized Media, Standard Personalization
- Allow your child to receive crossplay invitations: Allow, Don’t Allow
- Allow your child to show read receipts on the PlayStation App: Allow, Don’t Allow
Settings applied to PS5
- Data your child provides: Full, Limited
Settings applied to PS4
- Who can see your child’s activities: No One, Friends Only, Friends of Friends, Anyone
- Who can follow your child: Friends Only, Anyone
- Who can see your child’s followers: No One, Friends Only, Friends of Friends, Anyone
- Who can see the players your child follows: No One, Friends Only, Friends of Friends, Anyone
- Who can send your child a request to watch: No One, Friends Only
How to use the PlayStation Family app
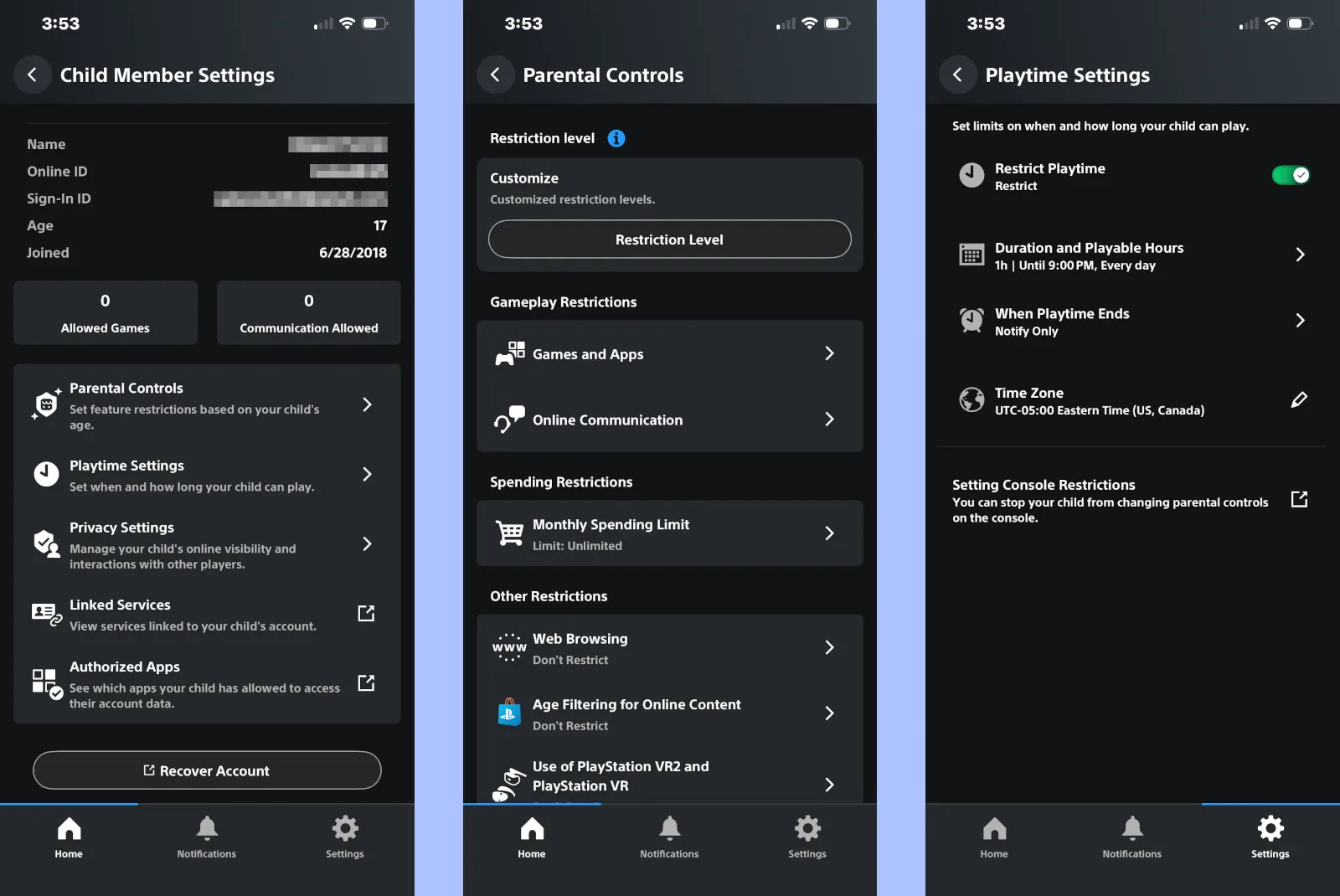
The PlayStation Family app is a new, easier way to manage your accounts. Some settings take you to the web portal anyway, but at least most of what you need is contained within an easy-to-use interface.
Step 1: Download and install the PlayStation Family app.
Step 2: Open the app and select Turn Notifications On or Not Now to get started.
Step 3: Sign in to your PSN Account. The app may automatically sign you in if you’re already logged in to the PlayStation App.
The app consists of three tabs: Home, Notifications, and Settings. The Home tab info is specific to the child account you select at the top. Here’s a rough breakdown of each tab:
Home
- Playtime for Today chart
- Playtime Settings: Set up and modify
- Activity chart
- View All Activity
- Monthly Spending Limit
Notifications
- All notifications you receive appear in this tab
Settings
- Family Management: See your accounts, add a child, add an adult
- Push notifications: Enable/disable for Playtime and Parental Controls
- Feedback: Complain to Sony about the number of times you have to log in
- Account Information: Your account info
- Service Status: Current status of all PlayStation services
- Support: Get help
- App and Legal Info: Yawn
So, let’s backtrack to the Home tab and select the “slider” Child Member Settings icon next to the child’s name.
More about Child Member Settings
Here you’ll see your child’s info, like their Sign-In ID, Online ID, the number of allowed games, and so on. There are also five sections that we’ve already customized to some degree on the console and in a web browser. I’ll be brief about each except where they’re different from the other interfaces.
Parental Controls
- Restriction Level
- Games and Apps
- Online Communication
- Monthly Spending Limit
- Web Browsing
- Age Filtering for Online Content
- Use of PlayStation VR2 and PlayStation VR
- Parental Controls on PC
Playtime Settings
- Restrict Playtime on/off
- Time Zone
- Setting Console Restrictions: Prevent the child from changing parental controls on the console
Privacy Settings
- Privacy Settings Set By: Parents/guardian, Child
- Privacy Profile (see above)
- The remaining privacy settings are already defined in the web browser instructions shown above.
Linked Services
- Takes you to your child’s PSN Account web page listing all linked services, but within the app
Authorized Apps
- Takes you to your child’s PSN Account web page listing all authorized apps, but within the app.
Recover Account
- Takes you to your child’s PSN Account web page to reset the password, but within the app
-
Best overall
 LastPass
LastPass- One-to-one sharing
- Secure notes
- Basic customer support
-
Best for Apple devices
 1Password
1Password- Travel mode
- 365-day item history
- 24/7 email customer support
-
Best for usabilityDashlane
- Password sharing
- Personalized security alerts
- 50-password limit
Data effective 12/01/25. Offers and availability may vary by location and are subject to change.
Our pick: Which password manager is best?
LastPass is our go-to solution for the best password manager. It checks all the right boxes: desktop and mobile support, password sharing, file storage, family management, dark web monitoring, a password generator, and more. It feels more complete overall, thanks to a good balance of free and premium features.
Get the best internet to complement your password manager
Many internet providers now include a free security suite when you sign up for new internet service. If it doesn’t, enter your zip code below to see what else is available in your area.
Compare password manager features and prices
| Best for | Service | Price* | Best features | Get it |
|---|---|---|---|---|
| Best overall | LastPass | Free–$48.00/yr. | View on LastPass | |
| Best for Apple devices | 1Password | $29.00–$45.00/yr. | View on 1Password | |
| Best for usability | Dashlane | Free–$60.00/yr. | View on Dashlane | |
| Best for business | Keeper | $39.99–$84.99/yr. | View on Keeper | |
| Best for budgets | RoboForm | $18.00–$28.65/yr. | View on RoboForm | |
| Best free option | Bitwarden | Free–$40.00/yr. | View on Bitwarden | |
| Best no-cloud password sync | Sticky Password | Free–$29.99/yr.; $79.99/life | View on Sticky Password |
*Non-business prices as of 12/01/25.
What should you look for in a password manager?
The best password manager should generate long, unique passwords that are nearly impossible to crack. It’s essential for day-to-day use across all accounts because passwords are often reused, too short, and easily guessed.
A password manager should also support multiple operating systems, like Windows and Android. Be sure to pick a password manager that is in active development and offers end-to-end encryption, if possible.
Finally, a password manager should list “zero knowledge” somewhere on its product page. That means the developer doesn’t have access to your data. If a password manager advertises device synchronization (most do), that data should reside on the developer’s cloud servers as an inaccessible encrypted blob.
For a more in-depth look at the essential features to consider in a password manager, jump ahead to our expanded section below.
Best overall: LastPass

Pricing
- Free
- Premium: $36.00/yr. (1 user)
- Families: $48.00/yr. (6 users)
- Teams: $48.00/yr. (per user)
- Business: $84.00/yr. (per user)
Features
- Password generator
- Password autofill
- Secure vault
- Password sharing
- Encrypted notes
- Two-factor authentication
Availability
- Desktop: Windows, Mac, Linux
- Browser extensions: Chrome, Edge, Firefox, Opera, Safari
- Mobile: Android, iPhone, iPad
View on LastPass
LastPass is an excellent password manager for storing everything you need, from login credentials to addresses to credit cards.
The free version offers up the basics, such as unlimited passwords, password sharing with a friend or family member, two-factor authentication, a password generator, and password autofill.
The drawback, however, is that the free service locks users into one device type—a computer or a mobile device, but not both. Users can switch between the two device categories, but only three times.
The Premium and Family plans, naturally, remove the device type limitations. The Premium plan targets a single user and adds 1GB of cloud storage, dark web monitoring, fingerprint and YubiKey support, a security dashboard, and the ability to share passwords with more than one friend or family member.
The Family plan targets six users and builds upon the Premium plan with unlimited shared folders and family management.
 Pros:
Pros:
- Unlimited password storing
- Password sharing
 Cons:
Cons:
- No monthly payment option
- Only one device type supported on the free version
Best for Apple devices

Pricing
- Individual: $29.00/yr. (1 user)
- Families: $45.00/yr. (5 users)
- Teams Starter Pack: $19.95/mo. (10 users)
- Business: $96.00/yr. (per user)
Features
- Unlimited devices
- Unlimited passwords
- Password generator
- Custom vaults
- 365-day password retrieval
- Password sharing
Availability
- Desktop: Windows, Mac, Linux
- Browser extensions: Chrome, Firefox, Edge, Brave, Safari
- Mobile: Android, iPhone, iPad
- Command-line options
View on 1Password
1Password launched in June 2006 and is similar to LastPass in terms of features.
Like its competitor, 1Password allows you to store login credentials and other sensitive data like credit cards. However, because there is no free edition, you have premium features right from the start. These include 1GB of storage, support for an unlimited number of devices, technical support, and a Travel Mode that temporarily removes data from your devices when you travel to other countries.
The Family plan builds on the Individual plan by adding support for up to five individuals. Users can set permissions and create vaults for each individual without the need for separate subscriptions. Item history backup allows users to recover deleted or changed passwords up to one year before the current date.
You can add additional people to the Family plan for $1 per person per month.
 Pros:
Pros:
- Supports Face ID
- Allows you to create and share custom vaults
 Cons:
Cons:
- No free version
- No live chat or phone support
Best for usability: Dashlane
Pricing
- Free
- Premium: $60.00/yr. (1 user)
- Friends & Family: $90.00/yr. (10 users)
- Starter: $240.00/yr. (10 users)
- Business: $96.00/yr. (per user)
Features
- Password sharing
- Two-factor authentication
- Dark web monitoring
- Built-in VPN
- Autofill
- Unlimited passwords and devices on Premium plans
Availability
- Desktop: app.dashlane.com
- Browser extensions: Chrome, Chromium browsers, Firefox, Safari
- Mobile: Android, iPhone, iPad
Dashlane has been around since 2012. It’s not much different than the other password managers on our list, offering password storage, form and payment autofill, two-factor authentication, password generation, a digital wallet, and so on.
The Friends & Family plan allows users to add up to five other individuals. You can create a private account for each member and manage them all—along with the billing—through the dashboard. This plan costs $90 per year, although you can make monthly payments of $9 per month (unlike the other password managers on our list). The same goes with the Premium plan: $60 annually or $6.50 monthly.
All new accounts start users with a 30-day Premium subscription trial, expanding the services to unlimited passwords and devices. The Premium model also adds dark web monitoring and unlocks the built-in VPN feature to protect your data from eavesdroppers as it travels down the internet highways.
Dashlane still has a free version, from what we can tell, but you wouldn’t know it by looking at the website. You can find the features list buried in the support articles, which includes unlimited passwords, a password generator, two-factor authentication, and more.
 Pros:
Pros:
- Monthly plans
- Built-in VPN (Premium)
 Cons:
Cons:
- Storage for only 50 passwords on the free plan
- High price for families
Best for business: Keeper
Pricing
- Personal: $39.99/yr. (1 user)
- Family: $84.99/yr. (5 users)
- Business Starter: $24.00/yr. (per user)
- Business: $45.00/yr. (per user)
- Enterprise: $60.00/yr. (per user)
Features
- Private vaults
- Team management
- Shared team folders
- SSO integration
- Two-factor authentication
Availability
- Desktop: Windows, Mac, Linux
- Browser extensions: Chrome, Firefox, Safari, Edge, Opera
- Mobile: Android, iPhone, iPad
While Keeper Security does provide password manager plans for individuals and families, Keeper Business and Keeper Enterprise are great solutions for offices and corporations. They not only increase productivity by eliminating manual password entries but also help prevent password-related security breaches.
With Keeper Business, each user has a private encrypted password vault. All confidential information—whether it’s a file or a password—is stored as a record, each with a built-in password generator to create unique, stronger passwords as needed. Other features include shared team folders, team management, and activity reports.
Meanwhile, Keeper Security doesn’t provide pricing online for its Keeper Enterprise solution. This plan includes everything offered in Keeper Business along with automated team management, email auto-provisioning, SSO authentication (G Suite, Azure, Okta), developer APIs, and more.
 Pros:
Pros:
- SSO integration
- Two-factor authentication
 Cons:
Cons:
- Add-ons can be costly
- Dark web monitoring is extra
Best for budgets: RoboForm
Pricing
- Free
- Premium: $18.00/yr. (1 user)
- Family: $28.65/yr. (5 users)
- Business: $23.97/yr. (per user)
Features
- Unlimited passwords
- Password generator
- Password audit tool
- Emergency access
- One-click logins
- Cloud backup (Premium)
Accessibility
- Desktop: Windows, Mac
- Browser extensions: Chrome, Edge, Firefox
- Mobile: Android, iPhone, iPad
Siber Systems’ RoboForm has been around since 2000, although the Premium plan didn’t emerge until 2010.
The big selling point of this password manager is its fast account logins that use a single click or tap. It’s also inexpensive, making it one of the cheapest password managers on our list.
The free version is robust, supporting unlimited passwords, cloud backup, bookmark management, login shares, and more. RoboForm Premium builds upon the free version with priority live customer support and synchronization across an unlimited number of devices. A shared folder is tossed into the premium plan, while the emergency access component allows users to grant access to their accounts. The free model only enables users to receive emergency access.
The Family plan simply expands RoboForm Premium to five users.
 Pros:
Pros:
- Offers a free version
- Has one-click logins
 Cons:
Cons:
- No dark web monitoring
- No Linux desktop app
Best free option: Bitwarden
Pricing
- Free
- Premium: $10.00/yr. (1 user)
- Family: $40.00/yr. (6 users)
- Teams: $4.00/mo. (per user)
- Enterprise: $6.00/mo. (per user)
Features
- Unlimited passwords
- Password generator
- Self-host capability
- Two-step login
- Device synchronization
- Emergency access (Premium)
Accessibility
- Desktop: Windows, Mac, Linux
- Browser extensions: Chrome, Safari, Firefox, Opera, Edge, Vivaldi, Brave, Tor Browser, DuckDuckGo for Mac
- Mobile: Android, iPhone, iPad
- Command-line options
- Web app
If you’re looking for a great, free password manager, Bitwarden is the one to get. It’s open-source software, meaning you’ll see many more features in the free version than others on our list while keeping the Premium and Family plans highly affordable.
Unlike other password managers on our list, this solution syncs across all devices without needing a paid subscription. Moreover, it has a self-host component, meaning you can ditch Bitwarden’s cloud service and create your own local server to store and synchronize your encrypted data blob across devices.
The Premium plan adds 1GB of cloud storage and file sharing, emergency access, vault health reports, the Bitwarden Authenticator, encrypted file attachments, and support for additional two-step solutions like YubiKey. The paid Family plan increases the user limit to six.
 Pros:
Pros:
- Text sharing
- Self-host component
 Cons:
Cons:
- No monthly plans for personal accounts
- No biometric 2FA option
Best no-cloud password sync: Sticky Password
Pricing
- Free
- Premium: $29.99/yr. (1 user)
- Premium: $79.99 for life (1 user)
- Teams Premium: $29.99/yr. (per user)
Features
- Unlimited passwords
- Password generator
- Biometrics support
- USB portable version for Windows
- Secure notes
- Wi-Fi sync (Premium only)
Accessibility
- Desktop: Windows, Mac
- Browser extensions: Chrome, Chromium browsers, Firefox, Brave, Opera, more
- Mobile: Android, iPhone, iPad
The big selling point with Sticky Password is the ability to synchronize your encrypted data blob with other devices without the need for the cloud. Everything is synchronized locally using your local network, keeping your data off cloud servers for better peace of mind.
The free model includes unlimited passwords, an autofill tool, a password generator, two-factor authentication, secure notes, biometrics support, and a tool for creating a portable USB password manager for Windows devices. This latter feature allows users to install the password manager on a USB stick or memory card and access their encrypted login credentials on any Windows PC—no cloud access is required. That means no more saving passwords in a text file on your external storage device.
The Premium model adds the Wi-Fi sync component, although you can still use the cloud for backup and synchronization. Password sharing is another Premium ingredient, along with priority customer support. Finally, Lamantine Software will donate a portion of each Premium subscription to the Save the Manatee Club. Unfortunately, there is no Family plan made available at the time of this writing.
 Pros:
Pros:
- Wi-Fi sync option
- Biometric support
 Cons:
Cons:
- No Family plan
- No Wi-Fi sync in free model
Do you have the fastest, most secure internet connection?
If your internet provider doesn’t have the security options you need, enter your zip code below to see what’s available to you.
Password manager features
Password managers, in general, have identical core features. We go more in-depth with some of these basics so you have a better understanding of why they’re important.
Password generator
While having a password vault is great, chances are many of those passwords are repeated across services, are too easily guessed, or were unearthed in a data breach. A password generator is essential because it can create a strong, random password based on absolutely nothing. It’s just a long string of letters, numbers, and symbols that don’t link back to your favorite pet or TV show.
Of course, the iPhone, iPad, and Android will generate a password for you. However, using a universal password generator found in a password manager allows you to quickly apply new passwords across all devices.
Item sharing
Item sharing is an essential tool if you plan to share account credentials. A good example here is a streaming service like Netflix or Disney+, where someone inside or outside the household wants access to the service. Item sharing doesn’t just apply to passwords either: you could share notes, credit cards, and so on—any data you don’t want to transmit openly and unsecurely.
Dark web monitoring
The dark web is a part of the internet that is accessible only by specific web browsers. Search engines do not index these sites, so you won’t find them using traditional browsers like Chrome and Safari. It’s a place where users conduct activities behind the public-facing side (the open web).
That doesn’t mean these activities are instantly nefarious, but stolen user credentials are typically broadcasted, sold, and purchased on the dark web. The monitoring process scans these websites for anything related to end-users, like email addresses, passwords, credit card numbers, and so on.
Cloud storage
There are two aspects to this feature to consider. First, data is synchronized across devices using cloud storage. Developers don’t have access to this data—it’s just an encrypted data blob that’s uploaded and downloaded as needed.
As shown above, Sticky Password has a Wi-Fi option, while Bitwarden has a tool to create a local service. Regardless, uploading and downloading data is required for multidevice synchronization, whether it’s local or in the cloud.
Second, premium services typically provide general online storage to back up sensitive documents and send them as encrypted attachments. Examples would be tax forms, scanned personal ID cards (like your driver’s license), a Social Security card, a passport, and so on.
Emergency access
Being able to grant someone access to your password manager account is actually a good thing.
For example, you have accounts with Netflix, Hulu, Disney+, MAX, and so on. You’re presently tethered to a hospital bed, one of your kids wants to binge-watch the latest Marvel TV show at home, and Disney+ has signed you out. You can’t remember the password, and you now fear the Hulk-sized wrath you’re about to hear over the phone.
By granting access to your password manager, your adult significant other can sign in and obtain the service login(s) they need. LastPass allows you to give one individual access to your password manager. 1Password is different: It has a tool to create a PDF with the master password stashed inside.
Zero knowledge
When choosing a password manager, documentation should list this feature. “Zero knowledge” means that your data is inaccessible by the password manager developer, even if said data resides on their cloud servers. Because the encryption key resides on the end user’s device, there is no unpacking the data on the server-side. Cloud-based data is used only to synchronize multiple devices and is nothing more than a pile of digital junk for hackers.
As for master passwords, they’re stored locally on your device. When entered, passwords convert into a key that unlocks a data key that decrypts and encrypts the password vault. All of this happens on the device side, so developers have “zero knowledge” of unlocking and retrieving your data on both ends.
That doesn’t mean these activities are instantly nefarious, but stolen user credentials are typically broadcasted, sold, and purchased on the dark web. The monitoring process scans these websites for anything related to end-users, like email addresses, passwords, credit card numbers, and so on.
Our verdict
LastPass has been our favorite password manager for some time, and that likely won’t ever change even though developer LogMeIn discontinued multidevice synchronization in the free version.
Overall, LastPass is a solid pick as a free password manager, but it’s even better through its paid tiers, thanks to cloud storage, multidevice support, dark web monitoring, and emergency access.
Still, you really can’t go wrong with any of our recommended password managers. Just weigh your exact needs against what you’re willing to pay. If you want a free client, stick with Bitwarden. If you don’t mind an annual fee, LastPass is your best option, although 1Password comes in at a close second.
FAQ about password managers
Why should you use a password manager?
How does a password manager work?
Are password managers safe to use?
Go free or premium: Which is best?
Seriously, what is a data blob?
One of the hottest items of 2025 is the Nintendo Switch 2 console. It’s bigger and meatier than its predecessor, sporting far better graphics, a larger screen, and a more comfortable build.
And because Nintendo is more of a family-friendly brand than the competition, you know there are plenty of tools at your disposal to keep kids safe when they play any Nintendo console.
In this guide, I’ll show you how to set a system lock PIN if you’re more concerned about time limits than content and communication. If you need more control over what your children play and do on Nintendo’s consoles, I’ll list three other ways to set up parental controls, plus how to manage GameChat, the new chat tool exclusive to the Nintendo Switch 2.
Before we begin
The Nintendo Switch and Switch 2 do not require a Nintendo Account to play games offline—all you need is a local user account. Any parental controls you set locally apply to all users on the console, whether they’re owned by adults or children.
However, the local parental controls are limited. Features like play times, spending restrictions, remote parental control management, and online play require a Nintendo Account.
Having just one Nintendo Account may be ideal if you only have one console. Setting up a parent/guardian account and managed child accounts is the way to go if you have multiple consoles.
First, let’s dig into how you can set a simple system lock PIN.
How to set a system lock PIN
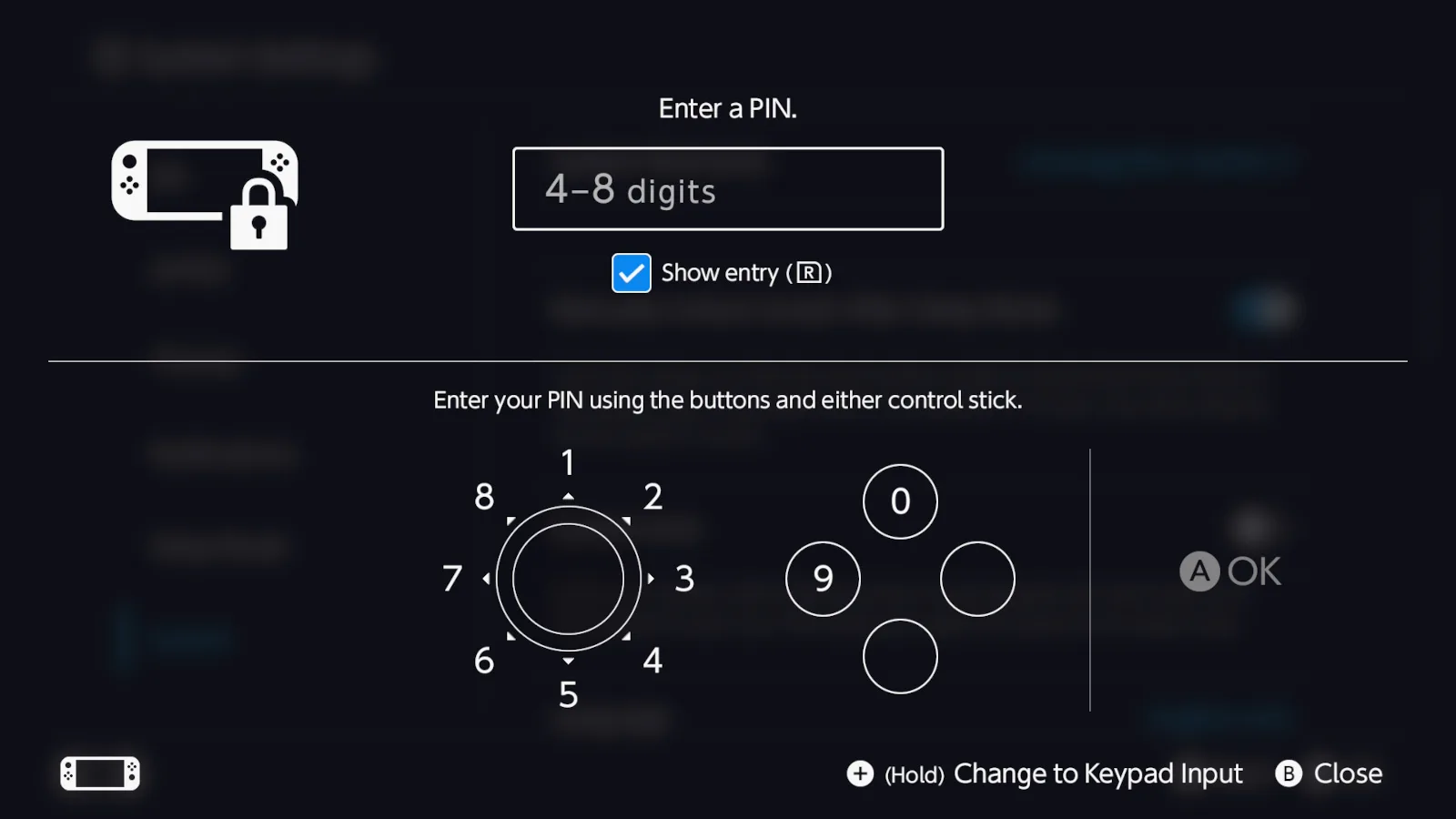
Use this feature if all you want to do is control when users can play the Nintendo Switch or Switch 2.
Step 1: Select the System Settings gear icon on the HOME Menu.
Step 2: Scroll down and select System.
Step 3: Select the System Lock toggle on the right to enable this feature.
Step 4: Select OK on the pop-up screen stating that you’ll need a PIN.
Step 5: Enter a four- to eight-digit PIN and then select OK.
Step 6: Re-enter the PIN again, and then select OK.
Need more control than a PIN lock? Let’s move on to how you can set the parental controls locally on the Switch and Switch 2 consoles.
How to set the parental controls without a Nintendo Account
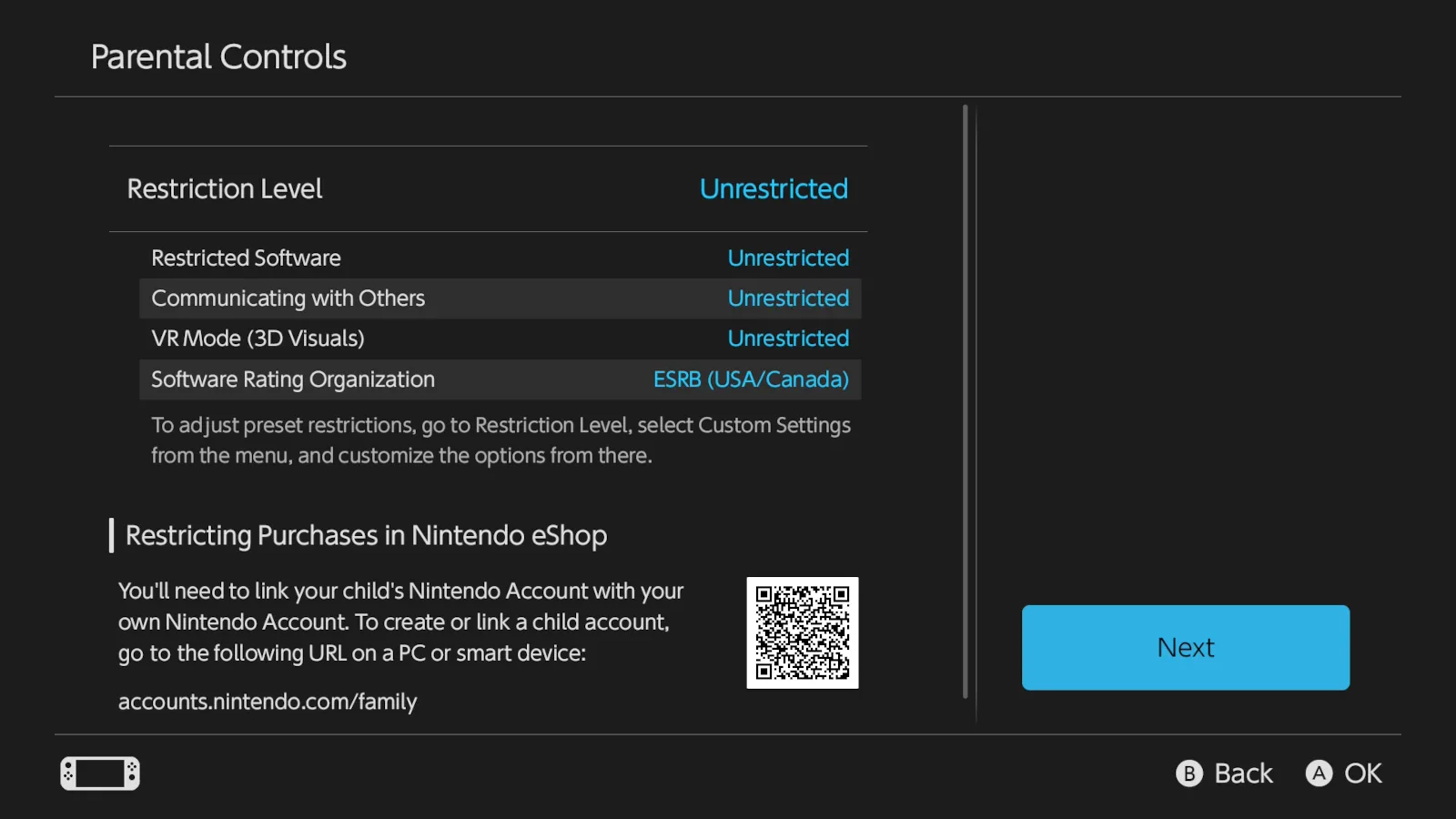
During the fourth step, you’ll see an option to scan a QR code and install the Nintendo Switch Parental Controls app. We’ll ignore the app and set the parental controls on the console itself.
Step 1: Select the System Settings gear icon on the HOME Menu.
Step 2: Select Parental Controls on the following screen.
Step 3: Select Set Up Parental Controls on the right.
Step 4: Select No Smart Device Available at the bottom.
Step 5: A pop-up message about accessing app-specific controls appears. Select Next.
Step 6: Set the Restriction Level (Unrestricted, Teen, Preteen, Child, or Custom Settings).
For Custom Settings, you have the following options:
- Restricted Software: Select “Unrestricted” or choose an age, such as “Rated for ages 15+”. The youngest you can set is “Rated for ages 3+”.
- Communicating with Others: Select this if needed, followed by the toggle on the next screen. Once enabled, you can toggle on and off the communication feature for each game.
- Restrict VR Mode (3D Visuals): Tap the toggle to turn VR mode on or off. This feature is used with headsets like the Nintendo Labo VR Kit. Nintendo says to turn this feature off if the console will be used by children under seven years old. Check out the Nintendo Labo page for more information about VR-compatible games.
- Software Rating Organization: Tap to change the rating system used in your region.
Select Next when you’re done.
Step 7: Create a four- to eight-digit PIN to lock the parental controls.
Step 8: Re-enter the PIN to confirm, then select OK to finish.
Do you have the best internet for Nintendo Online?
Your Nintendo Switch or Switch 2 console needs a Nintendo Account to use Nintendo Online. Enter your zip code below to find the best internet connection to play Splatoon 3 and other online-capable games.
How to set parental controls using a Nintendo Account on one console
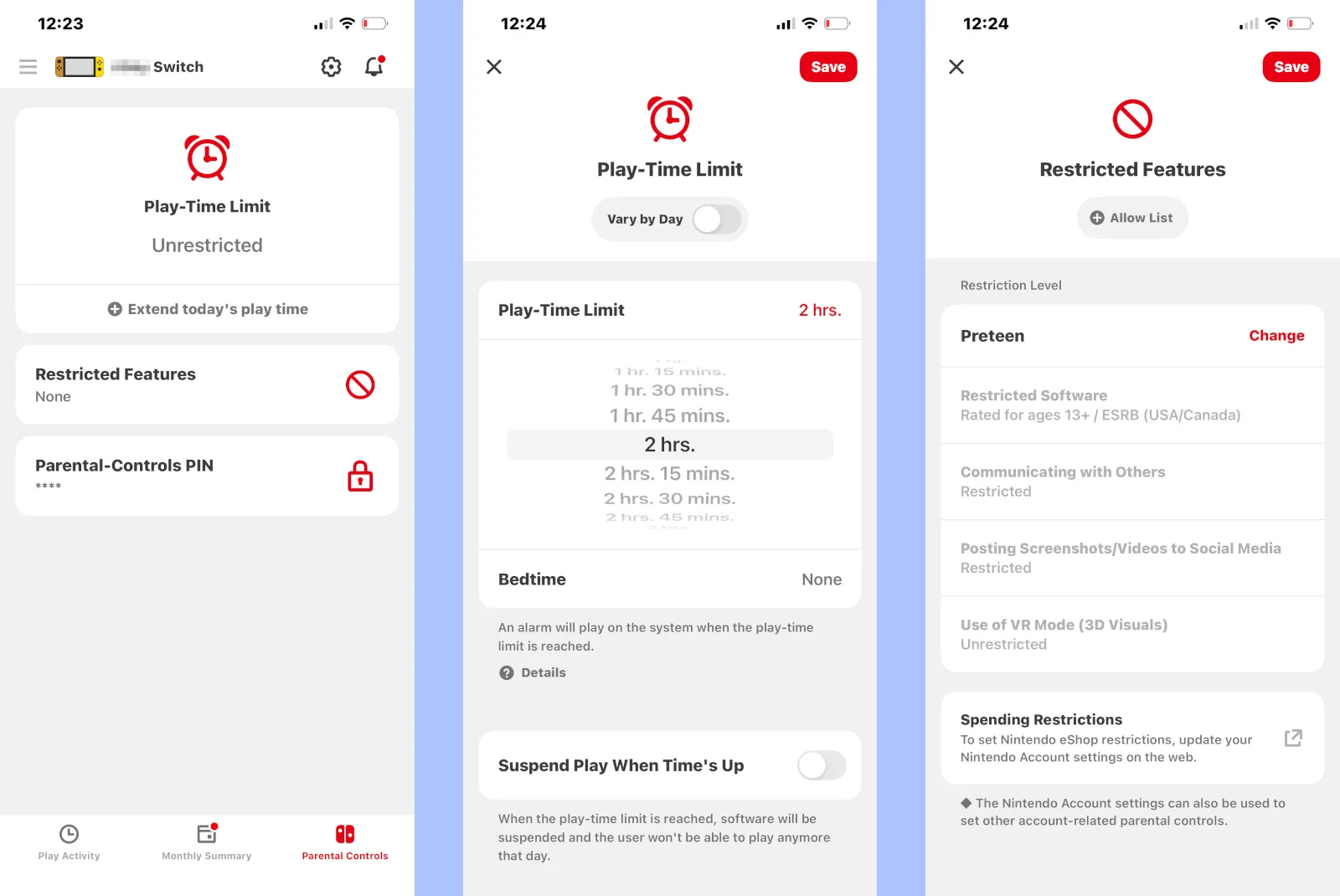
To play multiplayer games like Fortnite and Splatoon 3, you need a Nintendo Online subscription. To use the service, you need a Nintendo Account.
Keep in mind that if you create a Nintendo Account with unrestricted settings, every user account plays unrestricted. On the flip side, if you restrict specific games and features on the console, the restrictions apply to everyone who uses the console, not just kids.
That said, let’s create a Nintendo Account and we’ll go from there.
Create a Nintendo Account
Step 1: Go to the Nintendo Account page and select Create a Nintendo Account at the bottom.
Step 2: Enter your date of birth and then select Submit.
Step 3: Use Google or Apple to finish. Alternatively, enter a nickname, a valid e-mail address, a password, your gender, country, and time zone. Check the boxes to agree with Nintendo’s user agreement and privacy policies, and then select Submit.
Step 4: Choose your email preferences and then select Confirm & Register.
Step 5: Enter the verification code you received in an email to complete the setup.
Link your account and set the parental controls
Step 1: On the Switch or Switch 2, select the user account you’ll use to bind the console to your Nintendo Account.
Step 2: Select Sign In to a Nintendo Account on the following screen.
Step 3: Select Sign in with a QR code, which takes you to Nintendo’s login page. Alternatively, you can select Other Sign-In Methods.
Step 4: Select the Nintendo Account that will link to the console.
Step 5: Enter the verification code on the console and then select OK.
Step 6: Select Link to bind the console to your account.
Step 7: Select OK to finish.
Set the parental controls using the app
Now that the console is linked with your Nintendo Account, you need to bind the Nintendo Switch Parental Controls app too.
Step 1: Download and install the Nintendo Switch Parental Controls app.
Step 2: Open the app and select Start.
Step 3: Select whether you want to send or not send diagnostic data to Nintendo, and then select OK.
Step 4: Select Sign In/Create Account.
Step 5: Select Sign In (since we’ve already created an account) followed by the account you wish to use for binding the app to the console, then select Next.
Step 6: Move to the Switch or Switch 2 console and select the System Settings gear icon on the HOME Menu.
Step 7: Select Parental Controls on the following screen.
Step 8: Select Set Up Parental Controls on the right.
Step 9: Select App Has Been Installed.
Step 10: Select Enter Link Code.
Step 11: Enter the registration code you received in the app.
Step 12: Verify that the console is pairing with the correct account and then select Link.
Now that you have the app linked to the console, let’s see what you can do.
How to use the parental controls app
The Nintendo Switch Parental Controls app is divided into three tabs: Play Activity, Monthly Summary, and Parental Controls. The latter tab is where we want to begin.
Step 1: Select the Parental Controls tab.
Step 2: Select Play-Time Limit.
- Vary by Day (on/off): You can set when the restrictions apply on a daily basis, like easing restrictions on the weekends.
- Play-Time Limit: You can select Unrestricted or select the play time in 15-minute intervals up to six hours.
- Bedtime: None, or set the time between 4 p.m. and 11:45 p.m.
- Suspend Play When Time’s Up (enable/disable): No users can play games when the daily time is up.
Step 3: Select Save to complete.
Step 4: Select Restricted Features.
- Allow List: Add games that the Nintendo Account can play.
- Restriction Level: Your choices are None, Teen, Preteen, Child, and Custom Settings. These settings determine what the user can play, how they communicate with other games, how they post media, and use VR Mode.
Step 5: Select Save to complete.
Step 6: Select Spending Restrictions. This action takes you to accounts.nintendo.com within the app.
Step 7: Select the Nintendo Account you want to restrict.
Step 8: Select Spending Restrictions.
Step 9: Tap on the box under Spending/purchases on Nintendo Switch eShop and nintendo.com, and then select Save changes.
That’s it. You’re good to go. Game on. But wait! What if you have multiple consoles and need to manage each one? Move on to the next section if that’s the setup you need.
Do you have the best Wi-Fi for your Switch or Switch 2 console?
I’ve tested a boatload of standalone routers and mesh systems. If your Wi-Fi isn’t up to snuff, take a gander and my guide to the best gaming routers or the fastest routers I’ve tested.
How to set parental controls using a Nintendo Account on multiple consoles
We’ll assume you already created a parent/guardian account. Now we need to use your administrator Nintendo Account to create a Family Group and all the managed child accounts.
Having individual managed child accounts allows you to set restrictions based on their age. Plus, each child has access to the Nintendo Switch Online Family membership.
Create and manage a supervised Nintendo Account
Here we’ll create a Family Group and a child’s Nintendo Account that we’ll link to a Switch or Switch 2 console.
Step 1: In a browser, log in to your Nintendo Account.
Step 2: Select Nintendo Account Overview.
Step 3: Select Family Group.
Step 4: Select the Create Family Group button.
Step 5: Select Create an account for a child.
Step 6: Enter an account nickname, a sign-in ID, a password, date of birth, gender, and then agree to Nintendo’s privacy policy. Select Submit to complete.
Step 7: Move to the console and select the user account you want to bind to the child’s Nintendo Account.
Step 8: Select Sign in with a QR code, which takes you to Nintendo’s login page. Alternatively, you can select Other Sign-In Methods.
Step 9: Select the Nintendo Account that will link to the console.
Step 10: Enter the verification code on the console and then select OK.
Step 11: Select Link to bind the console to your account.
Step 12: Select OK to finish.
Alrighty then. Now that the child’s Switch or Switch 2 console is linked to their Nintendo Account, you’ll see them listed in the Nintendo Switch Parental Controls app. If you have another child with their own console, repeat the process, and the child will also appear in the app.
The next step only applies to the Nintendo Switch 2: Managing GameChat.
How to manage GameChat
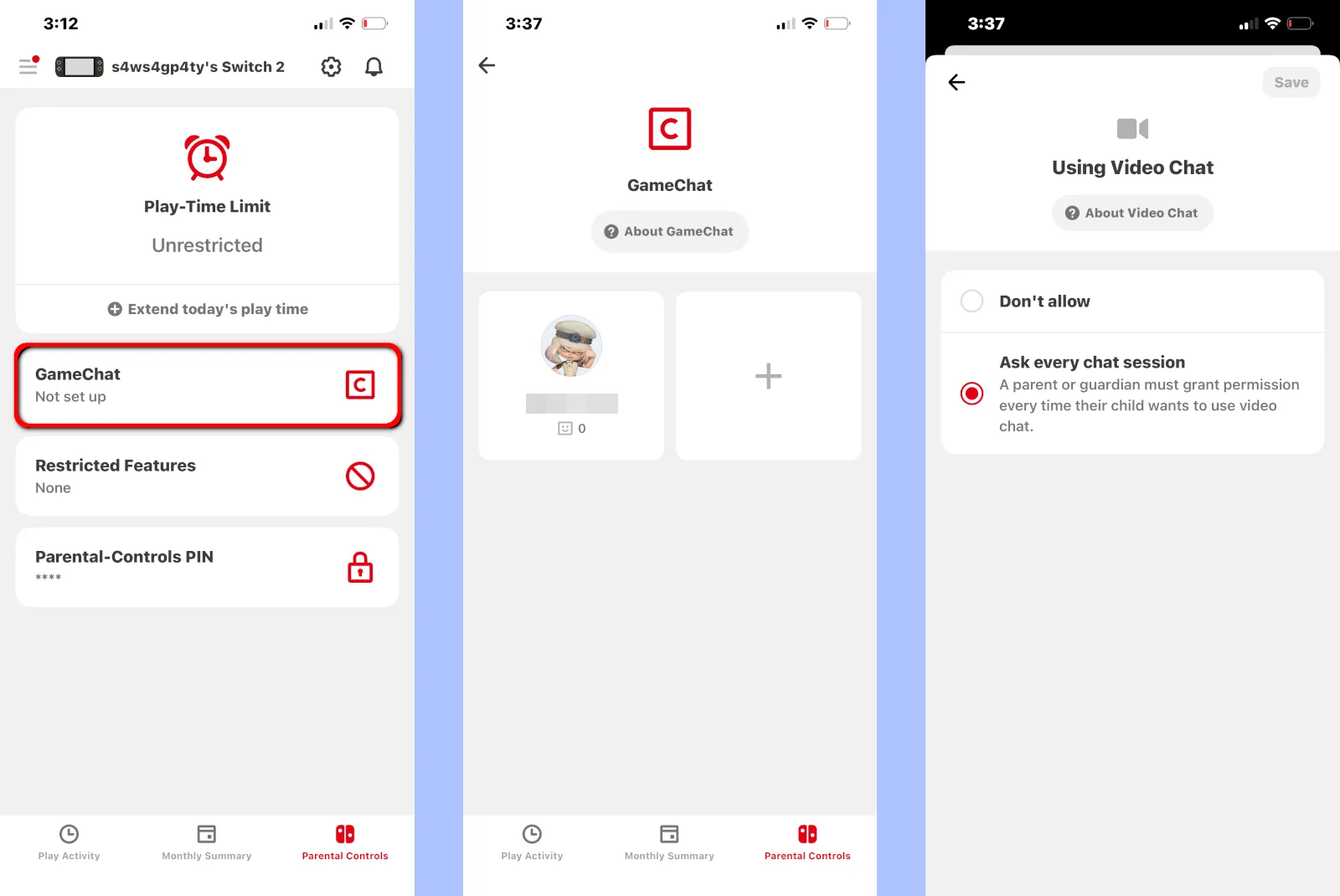
GameChat is a new feature introduced with the Nintendo Switch 2. It allows you to communicate with other Switch 2 gamers in real-time through voice or text. Setting it up requires a Nintendo Account, a Nintendo Online subscription, and a verification code.
Once GameChat is set up, you can set the approved friends for chatting. Next, you open GameChat, create a room, select your friends, and away you go. It uses the built-in microphone, but it also supports the Nintendo Switch 2 camera.
Keep in mind that if you’re the primary (adult) user of a Nintendo Switch 2 but a child created a user account on the console, you still need to set up parental controls to use GameChat. The feature will not start without parental controls enabled.
Here’s how to get started:
Step 1: Select GameChat on the console.
Step 2: Select the user account that will use GameChat.
Step 3: Select the Start button.
Step 4: Select Next after you read the intro.
Step 5: Agree to the terms and select Next.
Step 6: Consent to the terms and select Next.
Step 7: The app provides a verification code. Enter it into the console to finish.
Step 8: In the app, select the console (if it’s not already) followed by GameChat.
Step 9: Select the user account you just added.
When you link a child’s account, you won’t see anything but a blank friends list at first. The ellipsis icon next to the child’s name takes you to the Video Chat settings screen, where you can require the child to ask permission to use the video camera for each GameShat session.
Overall, here’s what you can do:
- Approve or deny friend requests
- Write yourself a reminder about each friend
- Don’t allow or require permission to use video during each chat session
- Set the camera’s field of view
- View the chat history
Updating your browser to the most recent version gives you access to the newest features and improvements, but most importantly, it protects your computer from attacks. Most browsers update automatically by default, but if your browser is out of date for any reason, you can manually update it by doing the following:
- Open your browser menu.
- Find your browser’s About page and select it.
- Click the update button.
- Close your browser and relaunch it.
Most modern browsers follow similar steps, but there are some minor differences in the menus and buttons. To learn more about the how and why of updating your browser, read on as we go into specific details.
Is it your browser or your provider?
If you’re experiencing long load times and unresponsive web pages, it could be a problem with your browser, or you might not be getting enough speed from your internet provider. Use our speed test to see the speed of your connection and other helpful information.
You can also install our mobile apps to test your speed on a smartphone!
Why should I manually update?
Ideally, you probably don’t want to be doing updates manually. In general, it’s a good idea to set your browser to download and install updates automatically in order to keep it protected from any recently discovered vulnerabilities or exploits. There are, however, a few situations where you might want more control over when these updates are downloaded. For example, some satellite plans give you extra data during low-traffic hours that you can use for downloading software updates and other large files.
Users might also want to manually update their browser proactively. Some browsers make new updates available days or weeks before they roll them out as automatic updates. If you want to know about updates as soon as they become available, you should follow your preferred browser’s developer blog, such as the Chrome Dev Blog.
In any case, find the method that works best for you to keep your browser as current as possible to avoid security threats online.
How to update Chrome
To update your browser when using Google Chrome, follow these steps:
- Open Chrome.
- Open the Menu (three dots in the top right corner).
- Select Help > About Google Chrome from the menu.
- Check to see if Chrome is up to date. If not, click Update Google Chrome.
- Close your browser and relaunch it to apply the update.
How to update Firefox
To update your browser when using Firefox, follow these steps:
- Open Firefox.

- Open the Menu (three dots in the top right corner).

- Select Help > About Firefox
- Click Restart to Update Firefox.
How to update Internet Explorer
Microsoft officially ended support for Internet Explorer 11 on June 15, 2022. That means that there will be no more official updates to the browser and thus you can’t update it, even if new security flaws are found. If you’re one of the last holdouts still using Internet explorer, it’s finally time to switch to another browser.
If any site you visit needs Internet Explorer, you can reload it with Internet Explorer mode in Microsoft Edge.
How to update Microsoft Edge
To update your browser when using Microsoft Edge, follow these steps:
- Open Microsoft Edge.
- Open the Menu (three dots in the top right corner).
- Select Help and Feedback > About Microsoft Edge.
- If an update is available, it will begin updating automatically.
How to update Safari
Apple has discontinued support for versions of Safari on non-Apple devices, so updating Safari is now integrated with upgrading your OS. To update your OS, follow these steps:
- Open the Apple menu in the top left corner of your screen.
- Select System Preferences.
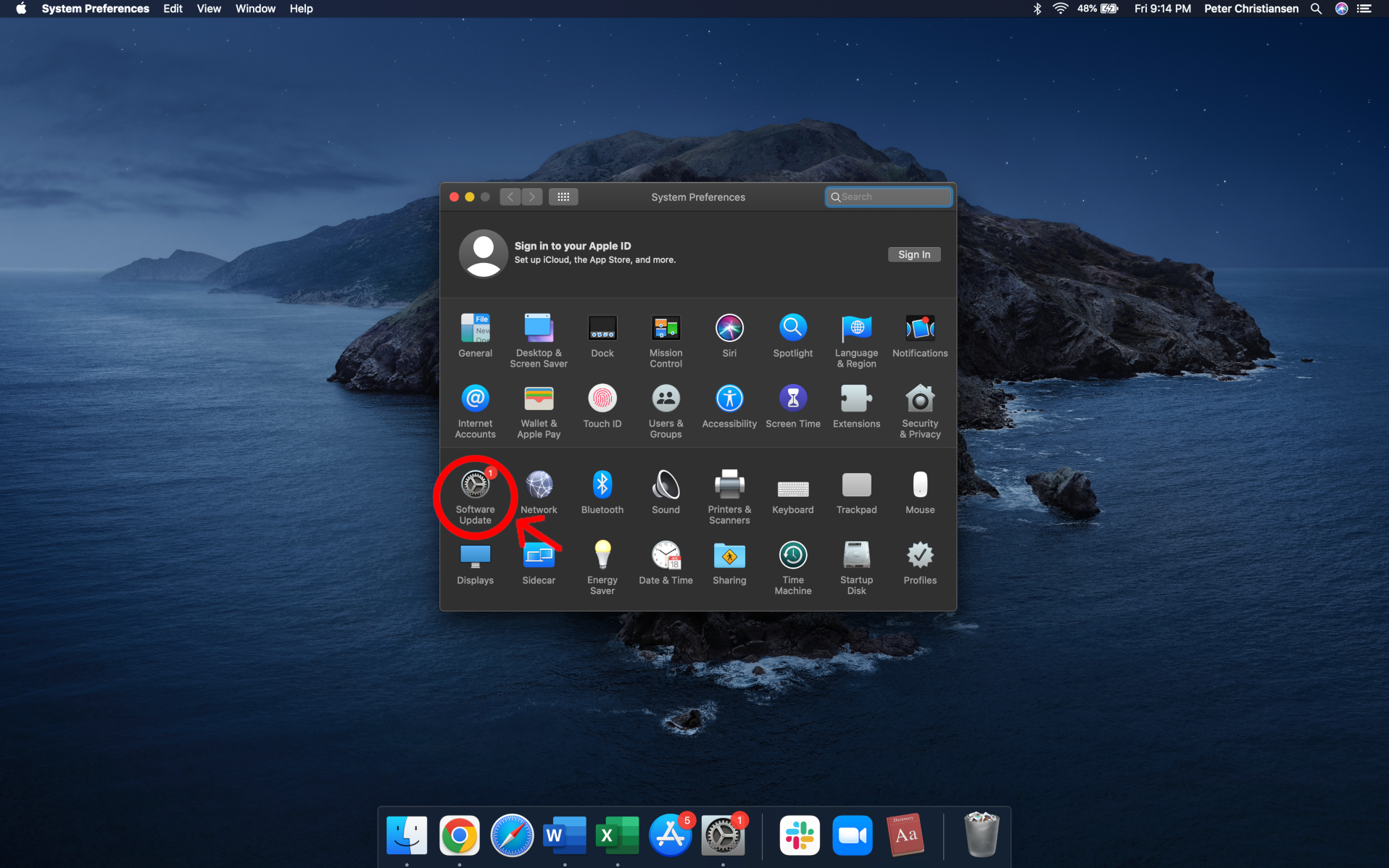
- Click on Software Update.
- Click Upgrade now to update your OS, including Safari, or select Automatically keep my Mac up to date to turn on automatic updates to keep it updated in the future.
Stay one step ahead of threats
Keeping your browser up to date is one of the easiest things you can do to stay safe online. Automatic updates are the best way to keep on top of new versions, but it’s good to keep an eye on updates and manually update if you have to.
For more information, check out these additional resources:
-
Best overallKurupira Web Filter
- Automatic web filtering
- Both blacklisting and whitelisting
- Time controls and scheduling
-
Best monitoring appLife360 Family Locator
- Geolocation tracking
- Place alerts
- Family Driving Summary
-
Best freemiumQustodio Free
- Free version with no time limit
- Web filtering
- Time controls
Data effective 8/27/2025. Offers and availability may vary by location and are subject to change.
Our pick: Which free parental control software is best?
The best free option for parental controls is easily Kurupira Web Filter. It gives you a huge amount of control over the content your kids can stumble upon online. It even has blacklisting and whitelisting options that many paid programs lack. There are no arbitrary limitations on the number of users or devices that can use it, and it doesn’t try to upsell you after a brief trial period. Unfortunately for Mac users, it’s only available on Windows.
Want more help keeping your kids safe online?
Free tools are great, but there are a few things parents need to know in their quest to keep their kids safe online.
1. Many devices and apps have their own parental control features
Whether you’re setting up a new iPhone or a new Netflix account, there’s a good chance you can control how your kids use it. Look for safety or security options in settings or accounts.
Learn About Parental Controls for iPhones, iPads, and Macs
Learn About Parental Controls for Microsoft Devices
2. Routers can be the best way to maintain safety for the entire household
The free solutions we recommend on this page are good for one device at a time, but most routers have tools that let you block or allow sites for every device on the home network. They usually let you set time limits by device, too, and may include bonus features like virus and malware protection. Router controls won’t help if your kid has access to a mobile line, but they’re a great place to start.
See the Best Routers with Parental Controls
Learn How to Set Up Parental Controls on Your Router
3. Your internet provider may offer security add-ons
Many internet service providers offer help with safety and security, whether it’s through the routers they offer or through add-on services. If parental controls and security are important to you, ask about them any time you consider switching plans.
The best free parental control software
- Best overall: Kurupira Web Filter
- Best monitoring app: Life360 Family Locator
- Best freemium: Qustodio Free
Need an internet connection that can keep up with everyone in your household?
See what providers are available in your area.
Best free parental control software
| Model/service | Price | Web Filtering | Devices | Get it | |
|---|---|---|---|---|---|
| Best overall | Kurupira Web Filter | Free |
| Unlimited Windows devices | Get for Free |
| Best monitoring app | Life360 Family Locator | Free |
| Unlimited iOS or Android devices | Get for Free |
| Best freemium | Qustodio Free | Free |
| 1 iOS or Android device | Get for Free |
Data effective 08/27/2025. Offers and availability may vary by location and are subject to change.
What should you look for in free parental control software?
When you’re looking for free parental control software, the first thing to look for is features that are free for good, not just part of a free trial. Freemium options can be good choices because, while they give you the ability to upgrade for more features, you still have a fully functional piece of software at no cost.
There are a lot of good free options out there, but each generally specializes in one or two things. You probably need different pieces of software for different purposes. If you want a single parental control system that covers all your devices and gives you all the tools you need for both mobile and desktop, you won’t find one for free.
If a more versatile option sounds worth paying for, check out our review of the best parental control tools to see if one of these options works for you.
Best overall—Kurupira Web Filter
Kurupira Web Filter
Specs:
- Automatic web filtering
- Blacklisting and whitelisting
- Time controls and scheduling
Kurupira Web Filter is a simple and robust program for setting up parental controls on your computer. Kuripira offers a wide range of parental control features:
- Web filtering
- Time scheduling
- Social media filtering
- Application blocking
- Activity reports
Importantly, while the default web filter uses a smart filter to block potentially inappropriate websites, Kuripira also gives you the ability to set up a blacklist (only blocking specific sites) or a whitelist (only allowing specific sites) for internet use. You can also opt to allow access to any website and simply enable tracking.
Kurupira Web Filter is Windows-only, so it can’t fill the role of a comprehensive parental control system across all your devices, but it’s a simple and powerful tool for setting up parental controls on your computer.
 Pros:
Pros:
- Full free version
- Robust, customizable features
 Cons:
Cons:
- Windows-only compatibility
Best location monitoring software—Life360 Family Locator
Life360 Family Locator
Specs:
- Geolocation tracking
- Place alerts
- Family Driving Summary
Life 360 is a location monitoring app that allows parents to keep track of kids while giving them the freedom to roam about on their own. It gives parents several tools, such as customizable alerts when someone reaches places like home or school, location history, and weekly reports to keep track of activity. Opting into paid versions gives you more locations and longer location hitsories.
Life 360 focuses on one thing, and does it well. Still, it lacks useful features you find in more general-purpose parental control apps. It doesn’t monitor or filter web activity on your child’s devices, it just keeps track of location. Even so, its geolocation features make it a great supplement to other parental controls or a simple solution for those who just want to keep track of their kids.
 Pros:
Pros:
- iOS and Android availability
- Real-time geolocation info
- Supports trackers like Tile
 Cons:
Cons:
- No web or activity monitoring
Best freemium filtering software—Qustodio Free
Qustodio Free
Specs:
- Cross-platform compatibility
- Screen time scheduling
- Smart web filtering
- Daily and weekly activity reports
Get for Free
Qustodio is one of the best paid parental control apps available, but it also has a free version. Unlike many parental controls with free trials that last only a few days, Qustodio’s free version lets you use it indefinitely.
Although the free version lacks many of the features you get in the full version, this parental control app still has features for both time management and web filtering. It also comes from an established and reputable company, so you don’t have to worry about an open-source project running out of steam or breaking with your next software update.
The biggest drawback to the free version of Qustodio is that it allows you to use it on only a single device—not particularly useful if you have more than one kid, or if your kid has access to multiple devices. On the other hand, this freemium business model allows you to upgrade to a paid plan if you find the free version useful enough that you’re willing to pay for additional features.
 Pros:
Pros:
- No expiration for free version
- Web filtering
- Time management tools
 Cons:
Cons:
- 1-device limit
- Limited features compared to premium version
Parental control features
Parental controls have a wide range of features. Many programs take a broad approach and try to do a little bit of everything, while others focus on one feature and try to do it better than everyone else.
If you limit yourself to free software, you don’t usually get the broad approach. Comprehensive parental control solutions usually require a paid subscription. Fortunately, there are excellent free options that focus on specific features, so thrifty parents can mix and match programs to get the most important features.
Web filters
Web filters are designed to block websites containing content that is inappropriate or potentially harmful for children. This can include malware, pornography, social media, instant messaging, and so forth. Any kind of automatic filtering suffers from two fundamental problems: overblocking or underblocking. Even customizable filters might block appropriate content while letting certain unwanted sites slip through.
The best content filters give parents the option to blacklist or whitelist individual sites. A blacklist blocks specific sites, while a whitelist allows access only to approved sites. Such fine-tuned controls take more work to manage properly, but they can make sure your kids don’t get locked out of the sites they need for their biology homework. It also can save you from listening to Baby Shark 50 times in a row.
Pro tip: Many routers come with built-in parental controls, such as web filters and time management tools. Buying a new router with parental controls can be a bit of an investment, but if your current router already has these features, setting them up doesn’t cost you a thing.
Activity monitoring
Web browsers keep an activity log by default, but activity monitoring software takes it up a notch, ranging from simply keeping a separate, uneditable browser history to detailed keylogging that captures every keypress and mouse click.
Depending on use, activity trackers can be either the most hands-off parental controls or the most invasive. Choosing a tracker instead of a web filter can show trust in your children’s judgment and allow them the freedom to go where they want on the internet. On the other hand, keeping a tight watch over everything they do can feel more intrusive than outright blocking content.
Pro tip: Keyloggers are most closely associated with computer hackers, who use them to steal passwords and other information from unsuspecting users. Some parental controls come with keyloggers, though in most cases, we’d consider this overkill.
The difference between these scenarios has less to do with the software itself and more to do with communication with your kids. When you have clear expectations and boundaries with your kids, monitoring software can be a way to build trust. If your kids feel like you’re spying on them, it can have the opposite effect.
Geolocation
Much like activity tracking, location tracking works best when you communicate with your kids. Most geolocation software has features that can help you set expectations and reduce the amount of effort it takes to keep track of your kids.
For example, geofencing and other location-based alerts let you know when your kids arrive at home, school, or work. Similarly, location history logs keep your kids accountable but don’t require constant monitoring.
Our verdict
If you’re a Windows user looking for parental controls, Kurupira Web Filter is the best free option we’ve seen. If you’re looking for parental controls for a Mac or mobile device, the free version of Qustodio is a solid choice, even if it doesn’t have all the features of the paid version.
Free parental controls FAQ
Is there a completely free parental control app?
Can you use free parental controls indefinitely?
Even on secure networks, cybercriminals still find ways to get in, and once they do, they potentially have access to anything and everything you do online. They use these vulnerabilities to steal your money, peer into your personal life, and perhaps even access live video feeds of your home. Terrifying, right? It’s the unfortunate reality of having so much of our lives integrated into technology.
The upside is Wi-Fi security is constantly improving, giving you some big guns to defend your home network. Once you combine your network’s built-in security tools with good network safety practices, you have a fairly robust defense against cybercriminals.
We’ll go over some of the ways hackers break into your network and show you what to look for in case of a security breach. Then, we’ll go over some essential preventive measures you can take to build up your own personal Fort Knox of Wi-Fi security.
Ready to see what's available in your area?
Enter your zip code to check out plans and internet providers in your area!
How hackers break into your network
Phishing
Phishing is a scam tactic used by hackers that tricks you into clicking on a malicious link or attachment that either installs malware on your device or persuades you to provide sensitive information, like login credentials. Phishing usually comes in the form of text messages or emails disguised as communication from reputable or familiar sources. Keep an eye out for urgent language pushing you to act fast—that’s a major red flag.
Here are some commonly used phishing attacks and warning signs you may run into:
- Claiming an issue with an account or payment
- Malicious login attempts
- Directing you to follow a link to fix a problem
- Asking you to download an attachment
- Asking for sensitive information
- Typos
Phishing usually relies on you taking the bait, so all you have to do is avoid clicking that fateful link or attachement. Approach all links and attachments with a healthy level of skepticism and be sure to always check the sender’s email address for anything that may raise an eyebrow.
Malware
Malware, short for Malicious Software, is any software designed to extract private information or harm your devices. These programs come in a variety of nefarious forms. Some record everything you type into your keyboard, searching for passwords. Others may intercept your web traffic, while some take pictures of your screen and send those back to the criminal. Some malware acts as a passageway for more malware. And sometimes, Malware is designed to simply mess up your computer.
You get malware by downloading files or clicking on links. Don’t download files from untrusted sources, and keep an eye out for disguised websites and emails. If you’re unfamiliar with a source, think long and hard before you let it through your network defenses.
Brute Force Attacks
Brute force attacks involve using a program to guess your password until it finds the right combination of characters. For a person, this is usually impossible without some type of hint, but computers can cycle through thousands of attempts without breaking a sweat.
How to protect your home network from hackers
There are many tools and practices at your disposal to protect yourself from malicious network attacks. Most are really easy to implement in your home network.
Create strong passwords
Your first line of defense is robust passwords that are not easily cracked by hackers. Many of us are guilty of creating simple passwords based on personal information like birthdays or names; it makes sense, as these are easy to remember, and being locked out of your accounts seems to happen at the worst times. But these passwords are also easy for criminals to decipher.
Sometimes, it doesn’t even take the use of malicious programs to break these passwords. Identifying information, like birthdays, pet names, and other personal details is often easy enough to find through a person’s public social media posts or profile information.
Best practice: The most secure passwords mix character types (numbers, letters, and symbols), contain at least 10 characters, and are not based on personal details (such as birthdays or pet names).
Change your router’s default login credentials
Router login credentials are not the same thing as your Wi-Fi name and password. Your router login credentials allow you to change your home network’s settings. These settings include your Wi-Fi password and your security settings.
Many routers come with default login credentials that are laughably insecure. In fact, the login credentials are usually something like “Admin” for the username, and the password is literally set as the word “password.” Even worse, the login page is almost always a universal URL web address or IP address. This lack of security makes it extremely easy for anyone on your Wi-Fi network to access your router settings if you haven’t changed the default credentials.
Best practice: To change your router login credentials, you’ll need to access your router’s settings; we detail the process in full in our guide on logging into your router.
In short, all you have to do is connect to your router via Wi-Fi or using an Ethernet cable and navigate to the settings page in a web browser using the router’s login URL; this is usually printed on a sticker along with the default username and password. Once logged in, you’ll be able to change the password. Alternatively, some routers use a mobile app instead of a web interface.
Some routers prompt you to change the login credentials when you first set up the router. If you can’t remember if you changed them already, it’s best to double-check.
Keep your router security enabled
Aside from limiting access to your network with a Wi-Fi password, your router also has built-in security measures. These should be on by default, so all you need to do is keep them running. Also, if you have a stand-alone modem and router, don’t connect to the modem directly via Ethernet, as this bypasses your router’s built-in security features. Instead, connect your devices to your router via Ethernet or Wi-Fi.
Upgrade to a WPA3 Router
WPA3 is the latest security protocol used in all Wi-Fi certified routers and devices since 2020. WP3 introduced many improvements in Wi-Fi security, notably better encryption and defense against brute force password-cracking attacks.
Best practice: If you don’t have a router that can use WPA3, it might be time to shop for a new one—which could even help your Wi-Fi speeds if your router is older. If your router was released after 2020, you should already have a WPA3 router. If your router was released earlier, it may use WPA2, which is not as robust as WPA3. WPA3 was announced in 2018, so if your router was made before then, it’s definitely not taking advantage of WPA3’s enhanced security.
Keep your computer and devices updated
Like most tech fields, cybersecurity advances at an extremely fast pace. So, while security tools are always improving, so are the methods of cybercriminals. Keeping your OS updated ensures you have the latest protections installed.
Best practice: Regularly update your devices and apps and consider turning on automatic updates to help you avoid forgetting.
Set up a Wi-Fi guest network
A guest Wi-Fi network allows others to use your Wi-Fi network while still protecting the most vulnerable parts of your network. For example, someone on the guest network may be able to browse the internet, but they can’t log in to your router and start changing network settings. This is a nice way to share your Wi-Fi without as much risk.
Best practice: Set up a guest network for when someone you don’t know well visits or accesses your Wi-Fi for any reason. You can follow our guest network guide to get your setup started.
Use antivirus software
No matter how diligent you are, sometimes malware still finds its way into your home network. But don’t fret—you can prepare for such occasions with antivirus software. Antivirus software not only works to keep malware and viruses off your computer and devices, but it scans and erases malicious programs that make their way through your other defenses.
Best practice: Find an antivirus software that fits your budget and needs. Luckily, there’s a wide variety of options nowadays. You can set your software to regularly scan your devices and make sure your personal data constantly stays secure.
I will never, ever tell you to disable the firewall on your computer. That’s just crazy talk right there. Doing so opens the door to hackers and malware, all eager to seize your computer and steal your data. Not fun.
But there may come a time when you need to disable the firewall on Windows or Mac temporarily to troubleshoot issues—and that’s my only exception. For this reason, I’ll show you where to disable and enable the firewall on Windows PCs, desktop Macs, and MacBooks.
A note before going in
The firewall on your Windows PC, Mac desktop, and MacBook is enabled by default. If you dig in and find that it’s been unknowingly turned off for some reason, chances are you already have some form of malware installed. I’d run a third-party virus scanner to clean out the malicious trash or perhaps even reset the device to its out-of-the-box state if the pesky bugs persist. Malware can slow your computer to a crawl and severely reduce your internet speeds, among other things.
How to enable or disable the firewall on Windows 11
You can take two paths to access the Microsoft Defender Firewall toggle. I will first give you Microsoft’s official instructions, followed by a shorter route using the hidden icons menu.
The Start button route
Step 1: Select the Start button.
Step 2: Select Settings on the Start Menu.
Step 3: The Settings panel appears on your screen. Select Privacy & Security on the left.
Step 4: Select Windows Security on the right.
Step 5: Select Firewall & network protection from the following list appearing on the right.
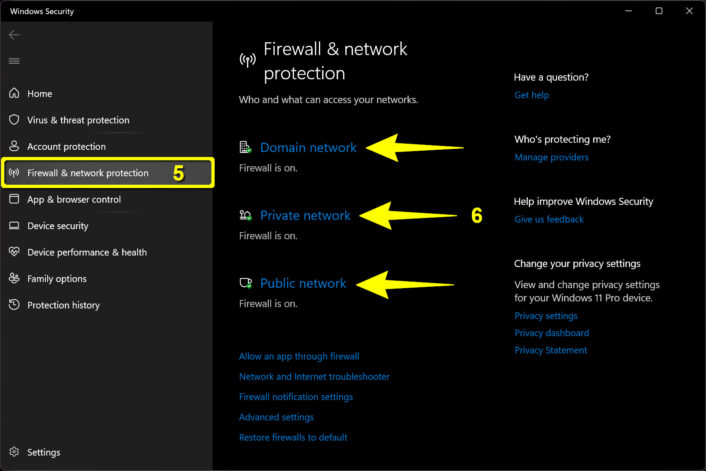
Step 6: The Windows Security panel appears on your screen with the Firewall & network protection category already selected. Choose Domain network, Private network, or Public network (see FAQ).
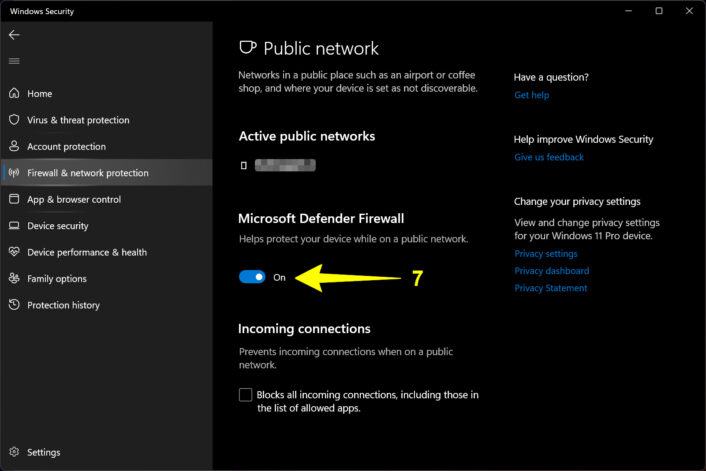
Step 7: Under Microsoft Defender Firewall, click on the toggle to set it to On or Off.
The hidden icons route
Here’s the shorter route to accessing the Microsoft Defender Firewall toggle. In my case, the Windows Defender icon resides in the hidden icons pop-up balloon. However, you may see the icon seated on the Taskbar instead.
Step 1: Select the Show hidden icons button (up arrow) on the Taskbar.
Step 2: Select the Windows Security icon.
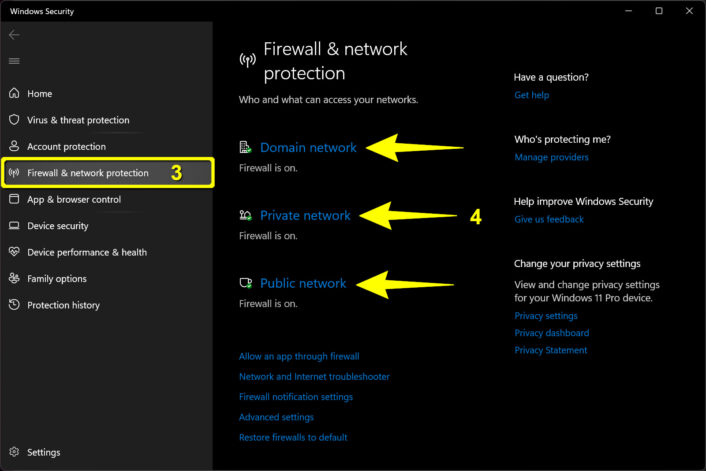
Step 3: The Windows Security panel appears on your screen. Select Firewall & network protection on the left.
Step 4: Select Domain network, Private network, or Public network (see FAQ) on the right.
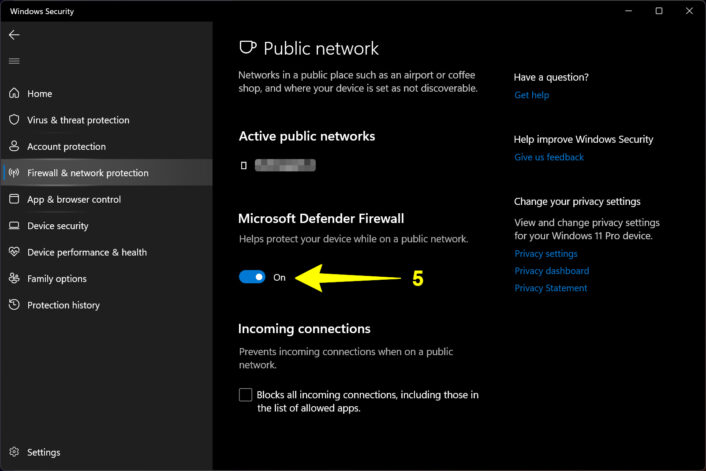
Step 5: Under Microsoft Defender Firewall, click on the toggle to set it to the On or Off position.
How to enable or disable the firewall on Windows 10
The instructions to reach the firewall toggle are different on Windows 10 than on Windows 11. But like Windows 11, you have two ways to reach the firewall toggle: using the traditional Start button method or the (faster) hidden icons route.
The Start button route
Step 1: Select the Start button.
Step 2: Select the Settings icon.
Step 3: The Settings panel appears on your screen. Select the Update & Security tile.
Step 4: Select Windows Security on the left.
Step 5: Select Firewall & network protection on the right.
Step 6: The Windows Security panel appears on your screen. Select Domain network, Private network, or Public network (see FAQ).
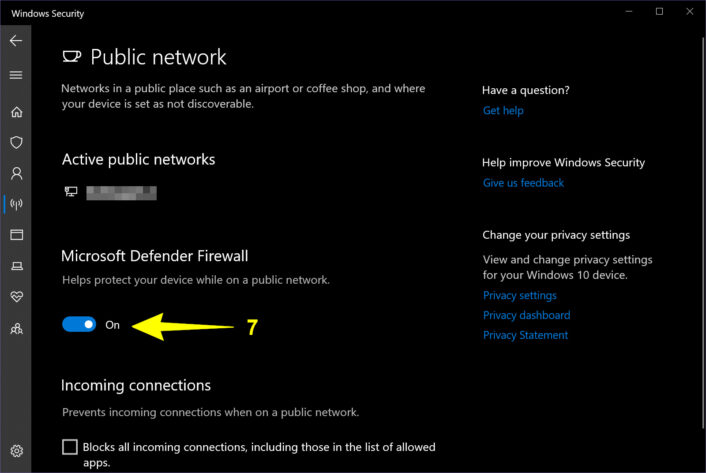
Step 7: Under Microsoft Defender Firewall, click on the toggle to set it to the On or Off position.
The hidden icons route
You can bypass the Settings window altogether and go directly to the Windows Security screen using these instructions.
Step 1: Select the Show hidden icons button (up arrow) on the Taskbar.
Step 2: Select the Windows Security icon in the pop-up menu.
Step 3: The Windows Security panel appears on the screen. Select the Firewall & network protection tile.
Step 4: Select Domain network, Private network, or Public network (see FAQ).
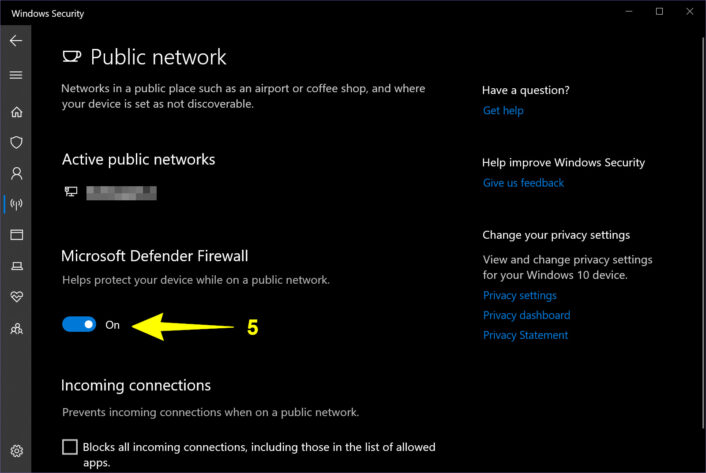
Step 5: Under Microsoft Defender Firewall, click on the toggle to set it to the On or Off position.
How to enable or disable the firewall on Mac
Apple keeps your route to the firewall toggle pretty simple, although you’ll have a faster trip if the System Settings icon is on the Dock. These instructions are based on macOS Ventura.
Step 1: Select the Apple menu icon in your screen’s top left corner.
Step 2: Select System Settings on the drop-down menu.
Alternative method: Select the System Settings icon if it appears on the Dock.
Step 3: The System Settings panel appears on your screen. Select Network on the left.
Step 4: Select Firewall on the right.
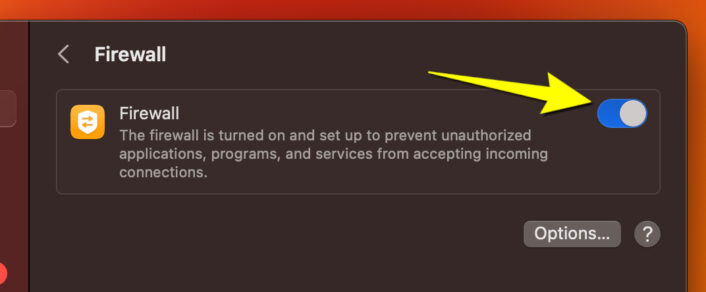
Step 5: Select the toggle to enable or disable the firewall.
FAQ about enabling and disabling a firewall
What is a firewall?
Should I turn off my firewall?
Can I temporarily disable my firewall?
When can I temporarily disable my firewall?
What are the Domain, Private, and Public profiles in Windows Defender Firewall?
Do smartphones and tablets have firewalls?
You don’t need a third-party subscription to manage children with an iPhone, iPad, or Mac. Apple provides easy-to-use parental controls with a quick tap or click on the Settings icon. From there, you can restrict specific apps, set purchase permissions, lock down the device for the night, and more.
I’ll explain how you can set up parental controls for the iPhone, iPad, and Mac.
Need more tools to keep your kids safe?
Apple’s parental controls are great, but they apply to Apple devices only. Check out our other guides for solutions you can apply outside the Apple ecosystem.
In this guide:
Create a child account | Parental controls overview | Enable Screen Time | Downtime | App Limits | Communication Limits | Communication Safety | Always Allowed Apps & Contacts | Content & Privacy Restrictions | FAQ
In this guide:
- Create a child account
- Parental controls overview
- Enable Screen Time
- Downtime
- App Limits
- Communication Limits
- Communication Safety
- Always Allowed Apps & Contacts
- Content & Privacy Restrictions
- FAQ
How to create a child account for iOS
Parental control settings aren’t device-specific. Instead, you create an Apple ID for your child you can manage from any Apple device. Once you create the account, you can use Quick Start to set up a new iPhone or iPad with your preferred parental controls already in place.
Here’s how to create a new child account from your iPhone, iPad, or Mac:
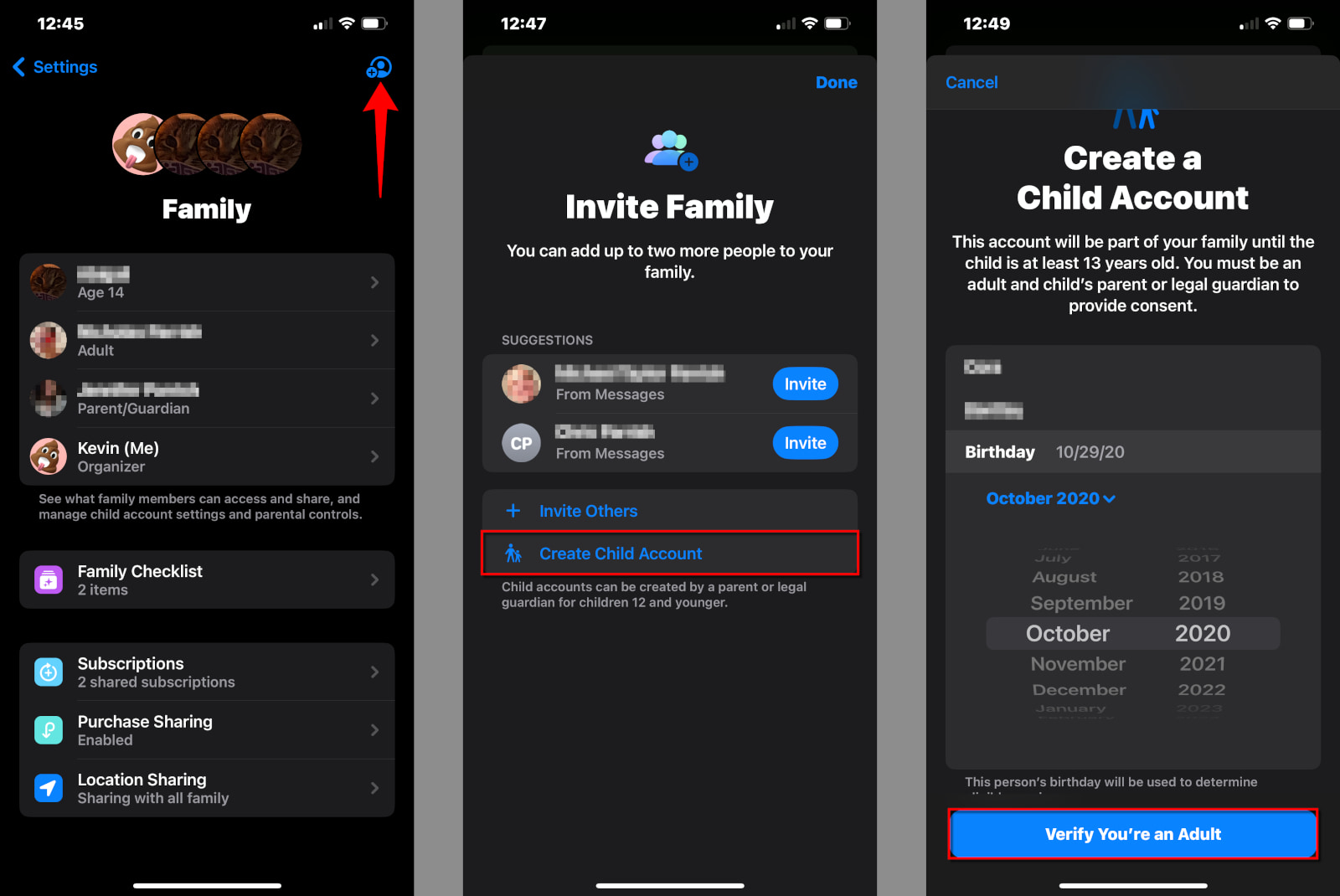
Step 1: Tap or click on Settings.
Step 2: Tap or click on Family.
Step 3: Tap or click on the blue Add Member button.
Step 4: Tap Create Child Account.
Step 5: Enter the child’s name, birthday, and then tap or click on Verify You’re an Adult.
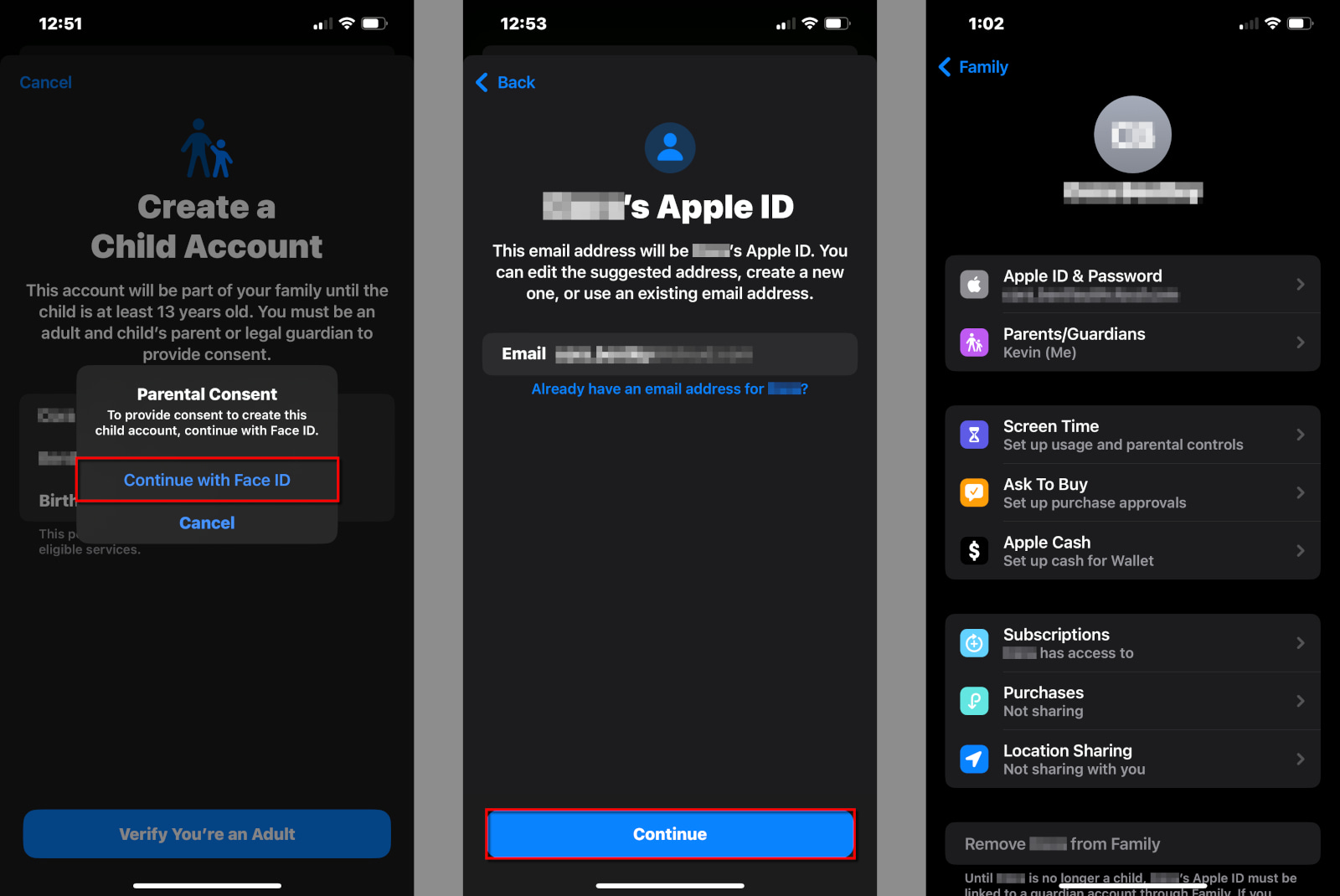
Step 6: Tap or click on the Continue With [security] popup to give parental consent. In my case, I used Face ID.
Step 7: Tap or click on Agree or Disagree for Apple’s Family Privacy Disclosure and its Terms and Conditions.
Step 8: Tap Continue to confirm the child’s new email address.
Step 9: Tap or click on the popup to verify the address.
Step 10: Create a password for the child’s new Apple ID.
Step 11: Choose a phone number to receive verification codes.
That’s it. You can use this Apple ID on any iPhone, iPad, or Mac you choose. Now, let’s take a deep, deep dive into the fathomless parental controls.
iPhone parental controls: a brief overview
You can manage children and monitor their activities by tapping or clicking through this path on your iPhone, iPad, or Mac:
Settings > Family > Your Child’s Name
Everything you need falls under the Screen Time category. Here is the list of tools provided to you—simply click on any of the following links to jump to instructions on how to modify each.
- Downtime
- App Limits
- Communication Limits
- Communication Safety
- Always Allowed
- Content & Privacy Restrictions (App Store, iTunes, Web browsing, Siri, Game Center)
However, before you begin, you must enable Screen Time on your child’s account before you can manage content and permissions.
Does your internet provider offer parental tools?
Many internet providers offer additional tools to help keep your kids safe online. If your provider doesn’t, enter your zip code below to see what’s available to you.
How to enable Screen Time
First, tap or click on the following path to reach the Screen Time settings:
Settings > Family > Your Child’s Name > Screen Time
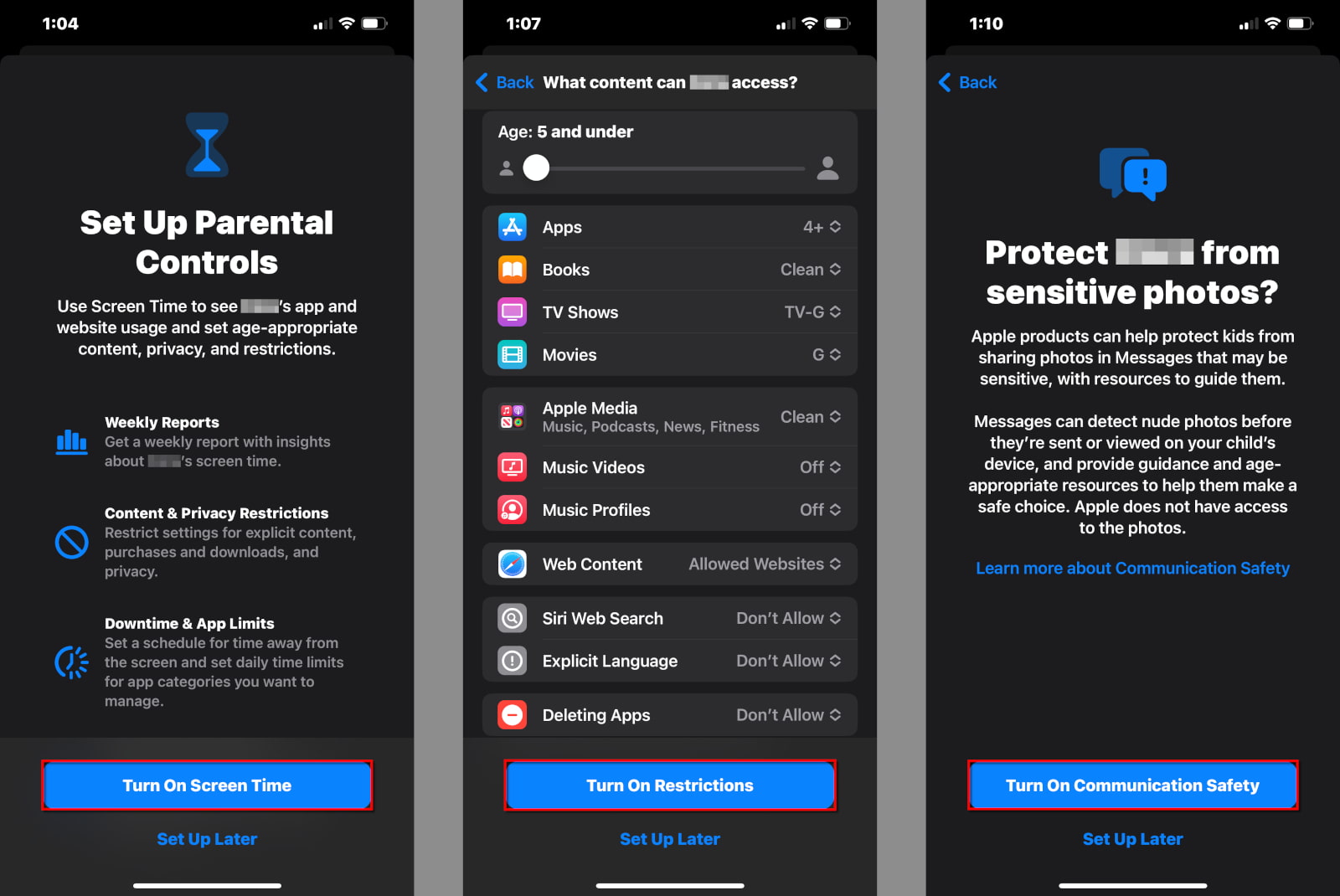
Step 1: Tap or click on Turn On Screen Time.
Step 2: A new screen appears, explaining all the available tools. Tap or click on Turn On Screen Time again.
Step 3: Tap or click on the slider to set the child’s age (5–18). The default settings adjust accordingly.
Step 4: Tap on a category to customize the content restrictions for Apps, Books, TV Shows, Movies, and more.
Step 5: Tap or click on Turn On Restrictions when you’re done. Alternatively, tap or click on Set Up Later to customize the restrictions some other time.
Step 6: Tap or click on Turn on Communication Safety to protect your child from sensitive photos displayed in the Messages app. Alternatively, you can tap or click on Set Up Later.
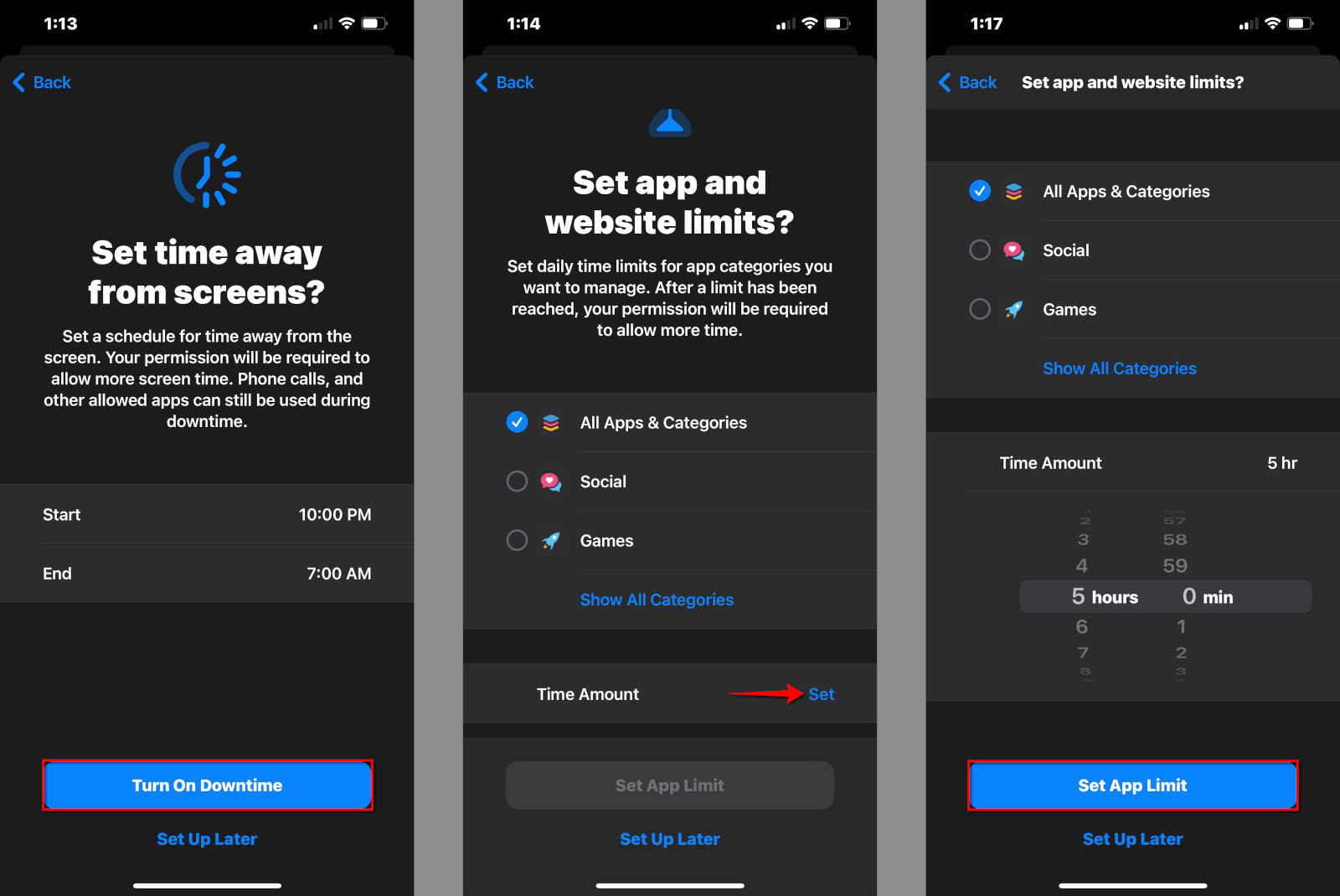
Step 7: Select a Start and End time period and then tap or click on Turn On Downtime. Alternatively, you can tap or click on Set Up Later if you need a customized Downtime schedule for your child.
Step 8: Set the daily time limits for your child’s apps. You can choose all apps and categories, select a specific category, or select apps individually.
Step 9: Tap or click on Set to define the Time Amount, and then tap or click on Set App Limit. Alternatively, you can tap or click on Set Up Later.
Step 10: Create a Screen Time passcode.
Step 11: Enter the Screen Time passcode again to complete the setup.
That’s it. Your child’s account is ready. If at any point you selected Set Up Later or need to adjust the settings, read on to find out how.
How to set your child’s downtime
Downtime is ideal when you want to block access to an Apple device during bedtime. Children receive a five-minute warning before downtime kicks in, allowing them to request more time if needed. Some apps and phone calls you choose elsewhere in the Screen Time controls will bypass the downtime restriction.
First, follow this path:
Settings > Family > Your Child’s Name > Screen Time
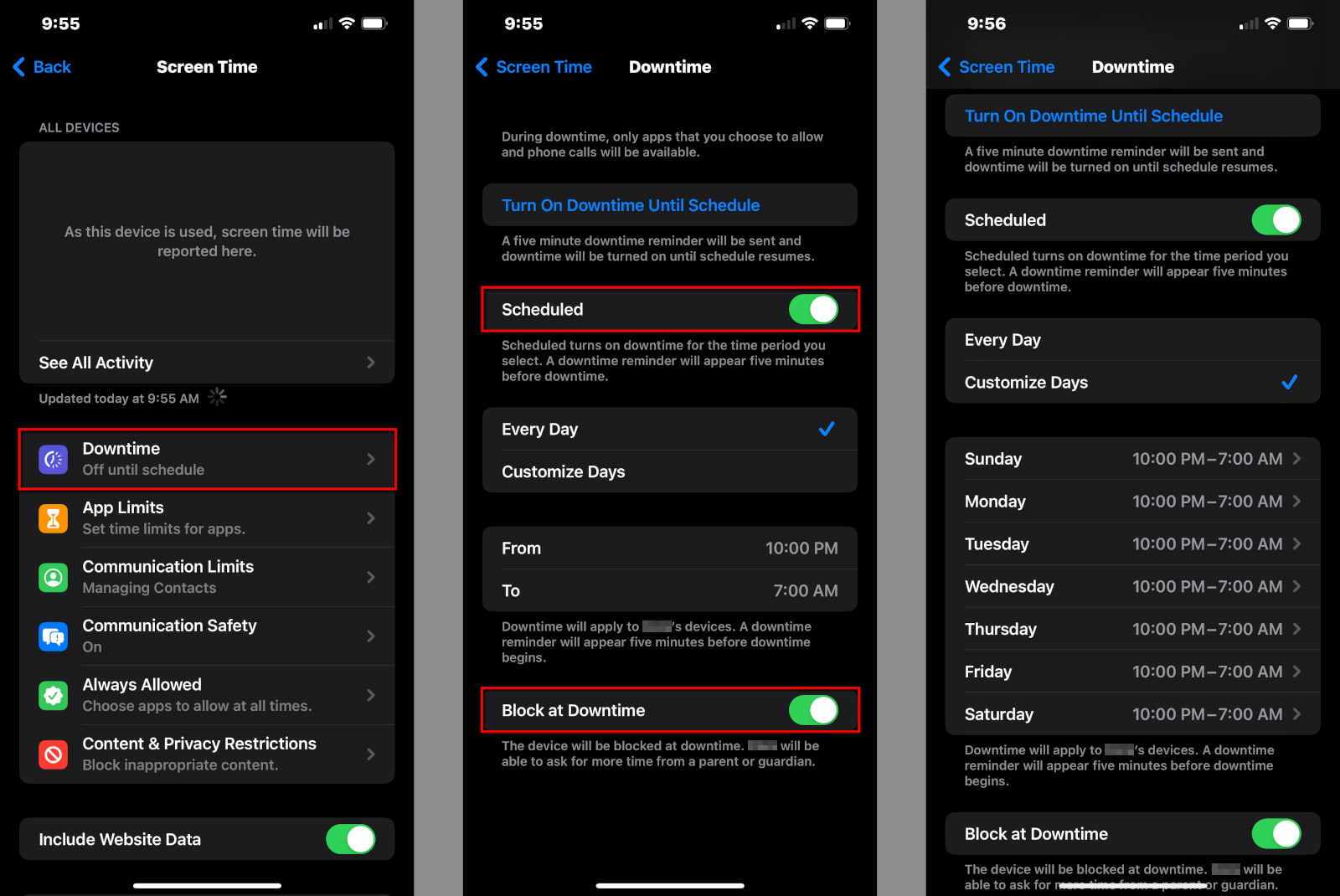
Step 1: Tap or click on Downtime.
Step 2: Enter your Screen Time PIN.
Step 3: Tap the Scheduled toggle to enable Downtime (green).
Step 4: Tap Every Day and select the start and end times, or select Customize Days and set specific times for each day.
Step 5: Tap the Block at Downtime toggle if you want to lock the device during Downtime. However, the child can ask for more time.
Keep in mind Downtime applies only once per day—you cannot schedule multiple Downtimes within a single day. If you need more than one block of time scheduled, use the parental controls in your router or gateway to block internet access for a specific time, like during homework hours.
How to set app limits
You can set daily time limits for any app installed on the child’s device. Tap on a category to limit all related apps or tap on a specific app. There’s an option to limit access to all installed apps too.
First, follow this path:
Settings > Family > Your Child’s Name > Screen Time
Step 1: Tap or click on App Limits.
Step 2: Tap or click on Add Limit.
Step 3: Tap or click on All Apps & Categories to set limits on all apps your child uses. Alternatively, tap or click on the circle next to a category (like Social) to select all social apps, or tap on a category to choose a specific app (like Discord).
Step 4: Tap or click on Next.
Step 5: Select the amount of time your child can use the app(s) each day. Alternatively, tap or click on Customize Days to set different time limits each day.
Step 6: Tap or click on Add to complete.
How to set communication limits
The limits you set apply to Phone, Messages, FaceTime, and iCloud contacts. Here you can restrict communication to Contacts Only, Contacts & Groups with at Least One Contact, or Everyone. To get started, follow this path:
Settings > Family > Your Child’s Name > Screen Time
Step 1: Tap or click on Communication Limits.
Step 2: Tap or click on During Screen Time to restrict who your child can communicate with during normal hours.
Step 3: Tap or click on During Downtime to restrict who your child can communicate with during Downtime hours. If you select Specific Contacts, a popup appears for you to select an existing contact or create a new one.
Step 4: Slide the Manage Child’s Contacts toggle into the On position to manage contacts remotely. A popup appears for you to select an existing contact or create a new one.
How to set communication safety
This setting only applies to the Messages app, which detects nude photos before they’re received and seen by your child. To toggle this setting on, follow this path:
Settings > Family > Your Child’s > Screen Time
Step 1: Tap or click on Communication Safety.
Step 2: Tap or click on the toggle next to Check for Sensitive Photos. It turns green when you enable this setting.
Step 3: Tap or click on the toggle next to Improve Communications Safety if you want to help Apple improve this tool (optional).
How to set Always Allowed apps and contacts
You can allow your child to use specific apps at all times and who your child can contact during Downtime. To change these settings, follow this path:
Settings > Family > Your Child > Screen Time
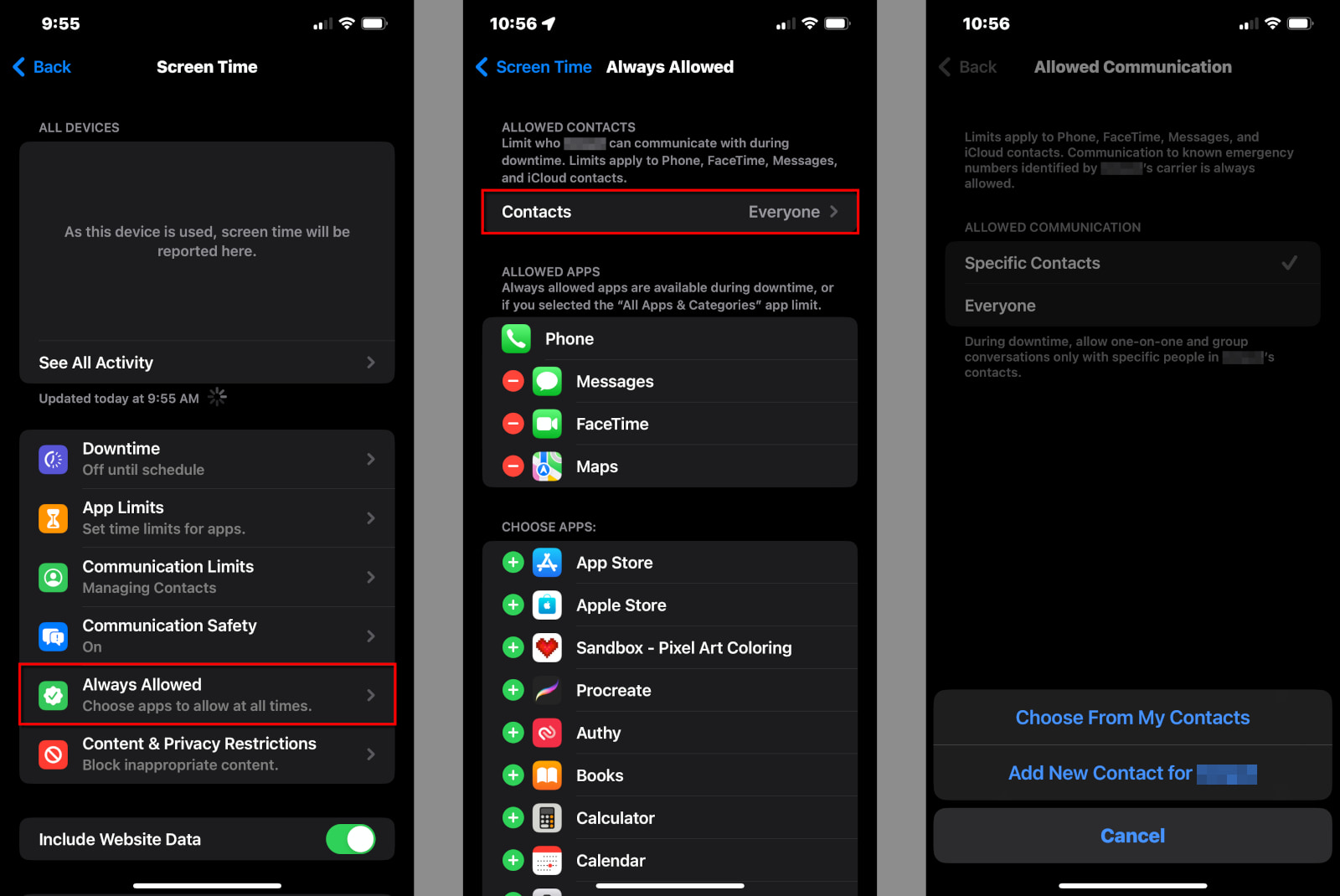
Step 1: Tap or click on Always Allowed.
Step 2: Tap or click on Contacts to select Everyone or Specific Contacts. If you choose the latter, a popup appears for you to select an existing contact or create a new one.
Step 3: Tap or click on any red “minus” icon to remove an app from the Allowed Apps list. Phone, Messages, FaceTime, and Maps are Always Allowed by default.
Step 4: Tap or click on any green “plus” icon to add an app to the Allowed Apps list.
How to change the Content & Privacy Restrictions settings
You need to enable this feature to manage how your child installs apps and makes in-app purchases. Here you can also block Apple-specific apps like Mail and Safari.
However, this section is fully loaded, so I’ll break it all down into six parts. To start, follow this path:
Settings > Family > Your Child > Screen Time
Step 1: Tap or click on Content & Privacy Restrictions.
Step 2: Tap or click on the toggle next to Content & Privacy Restrictions to enable this feature. It turns green when enabled.
iTunes & App Store Purchases | Allowed Apps | Store content | Web content | Siri content | Game Center restrictions
How to modify iTunes & App Store purchases
Here you can control what apps your child installs and deletes. You can also allow or block in-app purchases.
Step 1: Tap or click on iTunes & App Store Purchases.
Step 2: Tap or click on Installing Apps to Allow or Don’t Allow.
Step 3: Tap or click on Deleting Apps to Allow or Don’t Allow.
Step 4: Tap or click on In-App Purchases to Allow or Don’t Allow.
Step 5: Tap or click on Always Require or Don’t Require. If you select Don’t Require, your child isn’t prompted to enter a password again after the first purchase.
Step 6: Tap or click on Done when you’re finished.
How to modify the Allowed Apps list
Here you can enable or disable the built-in Apple apps, like Mail and Safari.
Step 1: Tap or click on Allowed Apps.
Step 2: Tap on the toggle next to any app you wish to enable (green) or disable (gray).
How to set Content Restrictions
This section provides all the settings you need to restrict movies, TV shows, websites, Siri results, and Game Center activity.
Step 1: Tap or click on Content Restrictions.
Step 2: The following screen breaks down into four cards and their individual settings:
Allowed Store Content
- Music, Podcasts, News, Fitness – Clean or Explicit
- Music Videos – Off or On
- Music Profiles – Off or On
- Movies – Don’t Allow, Not Rated, from G to NC-17, Unrated, Allow All
- TV Shows – Don’t Allow, from TV-Y to TV-MA, Allow All
- Books – Clean or Explicit
- Apps – Don’t Allow, from 4+ to 17+, Allow All
- App Clips – Allow or Don’t Allow
Web Content—Select one of three
- Unrestricted
- Limit Adult Websites – Tap the Add Website link for Always Allow or Never Allow to enable and block specific adult-oriented websites.
- Allowed Websites – Tap the Add Website link to add a website to the preselected list of nine (Disney, PBS Kids, National Geographic Kids, etc).
Siri
- Web Search Content – Allow or Don’t Allow
- Explicit Language – Allow or Don’t Allow
Game Center
- Multiplayer Games – Don’t Allow, Allow With Friends Only, or Allow with Everyone
- Adding Friends – Allow or Don’t Allow
- Connect with Friends – Allow or Don’t Allow
- Screen Recording – Allow or Don’t Allow
- Nearby Multiplayer – Allow or Don’t Allow
- Private Messaging – Allow or Don’t Allow
- Profile Privacy Changes – Allow or Don’t Allow
- Avatar & Nickname Changes – Allow or Don’t Allow
Other restrictions
Finally, on the Content & Privacy Restrictions screen, you can set restrictions to Allow or Don’t Allow for the following settings:
- Share My Location
- Passcode Changes
- Account Changes
- Cellular Data Changes
- Driving Focus
- TV Provider
- Background App Activities
Other spending tools at your child’s disposal
You can use two other tools besides Screen Time to manage your child’s spending.
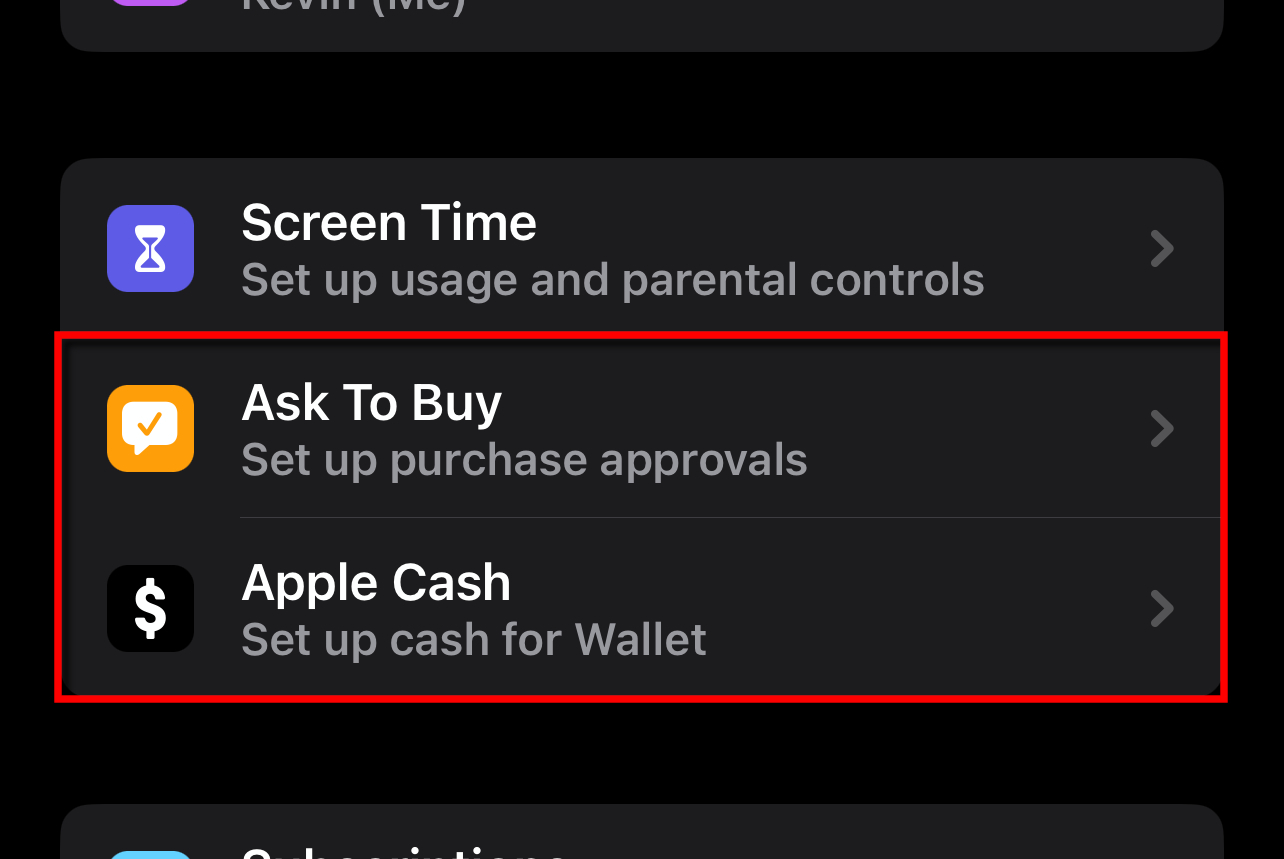
Ask To Buy
All Family members have access to the credit card on file when you allow Purchase Sharing. The Ask To Buy feature gives you more control over how your child purchases apps, in-app items, and media.
When your child selects an app or media to purchase, an Ask Permission prompt appears on the child’s screen. The child taps Ask—the parent approves or denies the purchase directly on their device.
Follow this route to enable Ask To Buy on the child’s account:
Settings > Family > Your Child > Ask To Buy
Ask to Buy purchases apply to App Store, iTunes Store, and Apple Books only.
Apple Cash
Apple Cash is an alternative to your child using the credit card on file. It’s a digital card you create for your child in Wallet and is used with any service that accepts Apple Pay. Your child can receive money through Apple Cash as well.
To get started, follow this path:
Settings > Family > Your Child > Apple Cash
Final call: Keep your guard up
I have lots of kids and oh boy can they be clever, especially young teens and older, who are a bit more resistant to your governing ways. I suggest a three-prong approach to parental controls as a failsafe in case something goes awry and your child streams questionable content until the roosters crow at dawn.
As I’ve shown in this guide, Apple provides an incredible toolset for parents at no extra cost. You can block access to your child’s Apple device overnight, restrict the content they consume, limit app use, and more.
Also, be sure to take advantage of the parental controls built into your router or gateway. Check out my guide on the best routers with parental controls if you need something a bit more secure than what you have now.
Finally, use your mobile provider’s tools to keep your child’s cellular use at bay, like AT&T Secure Family and AT&T Purchase Blocker.
FAQ about iPhone parental controls
Do the parental controls on iPhone, iPad, and Mac require a subscription?
Do I need to set the parental controls for each Apple device my child uses?
Do I need to set the parental controls directly on my child’s device?
From one parent to another: Don’t leave your kids unchecked online. The internet can be far more unsafe than the neighborhood they play in. Inappropriate content. Malicious software. Unsavory strangers. All of it makes me want to trash their devices and kick ’em outdoors (go get some sun, dangit).
The good news is that Microsoft Family Safety has your back if you own Windows, Xbox, and Android devices. This free service packs a slew of parental tools for keeping your kids’ content consumption and activities in check. Find out how to set up Microsoft’s parental controls and put restrictions in place.
In this guide:
What do you need? | Supporting platforms | Features | Create the parent account | Create a family group | Add a child | Settings and spending | Devices and Microsoft apps | Third-party apps | Block unwanted installs | Bottom line
In this guide:
What do you need to use Microsoft Family Safety?
You need the following two things to get started:
- A free Microsoft Account for the parent
- A free Microsoft Account for the child
You also need a browser or Microsoft’s app to manage and use the parental controls.
| Browser | Windows | Android | iPhone/iPad |
|---|---|---|---|
| Online dashboard | Microsoft Store | Google Play | App Store |
What platforms support Microsoft Family Safety?
You can use Microsoft Family Safety to manage the following platforms:
- Windows
- Xbox (which is really Windows with a controller-friendly interface)
You can also use Microsoft Family Safety to view activities on the following platforms:
- Android phones
- iPhone
- iPad
What can you do with Microsoft Family Safety?
Here’s what you can do with Microsoft Family Safety at no extra cost to you:
- Set device screen time limits on Windows and Xbox
- Set Microsoft app and game screen time limits on Windows, Xbox, and Android
- Filter out inappropriate apps and games
- Filter out inappropriate websites and content search in Microsoft Edge (blocks all other browsers)
- Allow/deny screen time requests (Windows, Xbox)
- Allow/deny content filter requests (Windows, Xbox, Android)
- Manage spending through a Microsoft Account
If you have a Microsoft 365 subscription, the following features are also available to you:
- See location alerts (iPhone, Android phones)
- View a teen’s driving habits (iPhone, Android phones)
- View a teen’s driving history (iPhone, Android phones)
Now, let’s get started!
Create the parent’s Microsoft Account
You need a Microsoft Account to use Windows and Xbox anyway, so skip this section if you already use these platforms and see how to create a family group.
If you’re new to the Microsoft family, you must have a Microsoft Account to activate and use Windows and Xbox.
The following instructions apply to everyone who will be managing the family group once it’s created. These are also web browser directions.
Step 1: Go to account.microsoft.com.
Step 2: Select the Sign in button in the top right corner.
Step 3: Select the Create one link on the following screen (shown above).
Step 4: Enter a valid email address, and then select Next (or create a new [email protected] address).
Step 5: Set your password and then select Next.
Step 6: Retrieve the security code sent to you, enter it into the required field on your screen, and then select Next.
Step 7: Solve the CAPTCHA to prove you’re not a robot, and then select Next.
Create a family group
Now that you have a Microsoft Account, it’s time to create the family group and add your child.
Step 1: Sign in to the Family Safety dashboard.
Step 2: Select the plus icon next to Add a family member in the top right corner (shown above).
Step 3: Select Organizer and then select Next.
Step 4: Enter your email address and then select Next.
Step 5: Solve the CAPTCHA and then select Invite.
Step 6: Open the Microsoft Family Safety email sent to you and select Join Now.
Add a child to the family
With the family group organizer set, you can now add a family member. For this set of instructions, let’s assume you need a new email address for your child.
Step 1: With the Family Safety dashboard open, select the Add a family member tile.
Step 2: Select Get a new email address on the following screen.
Step 3: Enter a username and select @outlook.com or @hotmail.com and then select Next.
Step 4: Create a password for the new account and then select Next.
Step 5: Enter the first and last name of your child and then select Next.
Step 6: Select the country/region and the child’s birthdate, and then select Next.
Step 7: Solve the puzzle and then select Next.
Step 8: Give consent for your child’s new Microsoft Account by entering your signature and selecting Yes, I agree.
Step 9: Give your child permission to use non-Microsoft apps with the account you created, and then select Continue.
Step 10: Set the age limits on apps and games, enable/disable activity reporting, enable/disable web and search filters, and enable/disable Ask to buy.
Step 11: To finish, select the Family Safety button.
Manage your child: Part 1
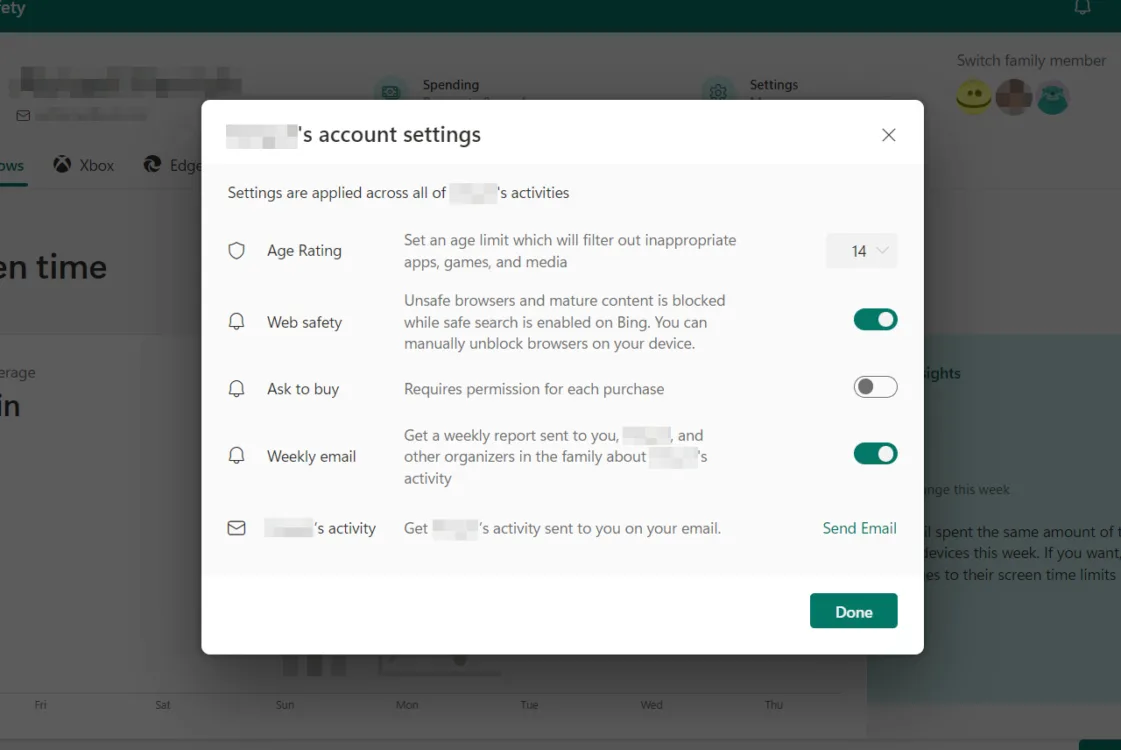
So, you have an organizer managing the family group, and your first child has been added. Everyone in the family group is displayed in tiles under Your family. As seen in the previous section, you already set restrictions. Now, you can go in and tweak the settings.
When you click on a child’s tile, you’re presented with two options and four tabs. First, I’ll cover the two options from left to right. I cover the tabs in the next section.
Spending
This section speaks for itself: Your child’s spending through Microsoft. At the top is a toggle for getting notifications about spending—I suggest you turn that on.
Here’s a brief rundown of what to expect on this screen:
Microsoft account balance: You can see what’s available and add money as needed.
Credit cards: Add a card for the child to use. Be sure to toggle on Require approval for every purchase to prevent an unwanted spending spree (it will happen).
Spending activity: This is a summary of all spending activity in the family group, not just the child’s activity.
Account settings
Although you already set the restrictions when you added the child, here is where you can modify them as they get older. Trust me: Your 14-year-old will complain if they’re still locked to Y7 content. (Stop all that growin’, dangit.)
Age Rating: Select an age from 3 to 20, or choose Any Age.
Web safety (on or off): Unsafe browsers and mature content are blocked. Safe search is enabled in Bing.
Ask to buy (on or off): Turn this on to prevent unwanted spending sprees.
Weekly email (on or off): Get a weekly report about the child’s activity for the week.
Child’s activity: Get a report about the child’s current activities. Select the Send Email link to get the report.
Now, let’s talk about the tabs.
Manage your child: Part 2
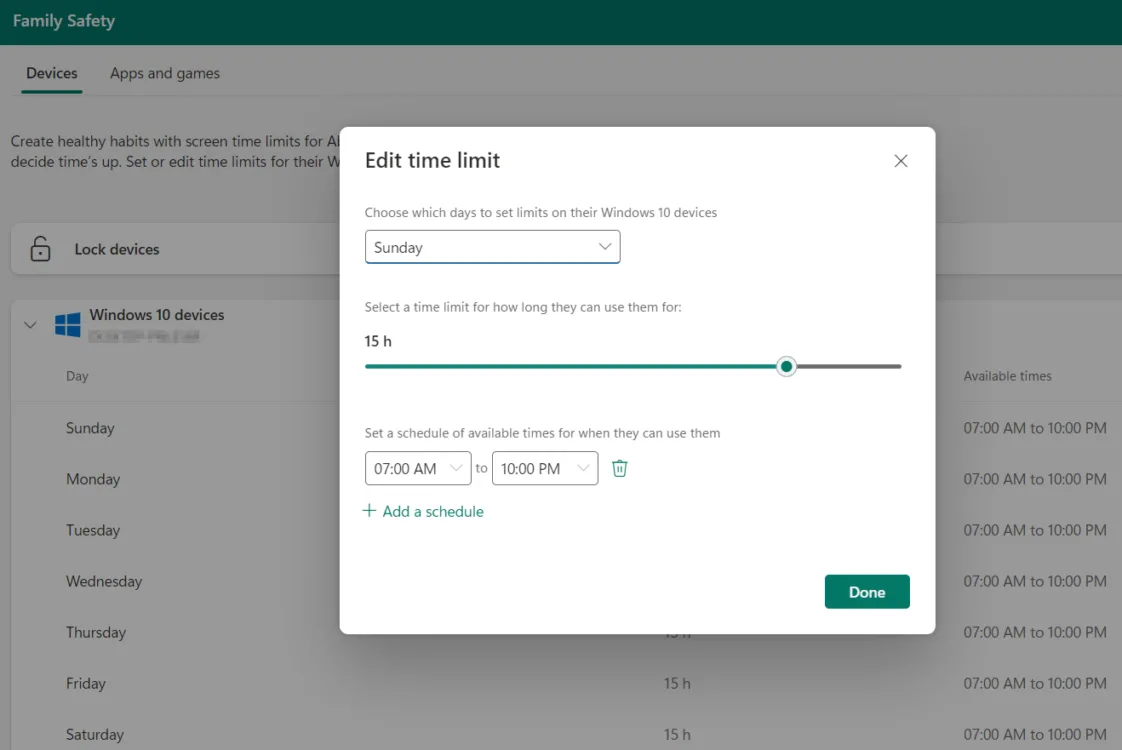
Windows and Xbox
The Windows and Xbox tabs have identical parental controls, so let’s take a look.
Screen time
Here, you’ll see a chart showing your child’s screen time on Windows 10 and Windows 11 (or Xbox).
At the bottom of the page, you’ll also see an Activity reporting toggle under Windows Settings (or Xbox Settings). Switch it on if you want to see your child’s app and game-related activities on every Windows device (or Xbox) they use.
Devices: Setting the time limits
At the top of this section is Lock Devices. Select it to lock and unlock each Windows-based device your child uses.
Below the Lock Devices setting is a chart that shows the daily time limits set for each Windows device (or Xbox) your child uses, as shown above. This is where you can set different or identical time limits throughout the week. For example, you may want to limit time during the week and give more time for the weekend. Here’s how:
Step 1: Select any day on the chart to edit the time limit.
Step 2: In the first field on the pop-up window, select up to six days you wish to enforce time limits or select Every Day.
Step 3: Move the slider to select up to 23 hours or choose No limit.
Step 4: Set the time when your child can use Windows. Select Add a schedule if you want to allow multiple time allowances during the day. A good example would be allowing screen time after school and later in the evening.
Step 5: Select Done.
Apps and Games: Setting the limits
At the top of this tab, you’ll find the App and Game limits toggle—turn it on. You’ll see a list of Microsoft apps and games installed on your child’s Windows device (or Xbox). Select one to see the user stats, block it, or set a time limit (similar to the instructions above).
To block third-party apps and games, refer to my instructions further down the page about managing consent.
Microsoft Edge
At the top of this tab you’ll see your child’s recent search queries and website activity. Everything you need to control what your child does through Microsoft’s browser is located under Filter Settings:
- Filter inappropriate websites and searches (on or off)
- Only use allowed websites (on or off)
- Add a blocked website
- Add an allowed website
- Activity reporting (on or off)
Mobile
iPhone/iPad and Android are managed by Apple and Google, respectively, so there’s very little you can do using Microsoft Family Safety on these devices. However, you can install the Microsoft Family Safety app (App Store, Google Play) and sign in with your child’s account on Apple devices and Android phones to see some activities.
| Android | iPhone/iPad | |
|---|---|---|
| Screen time | Yes | No |
| Apps and games activity | Yes | Yes |
| Location sharing | Yes | iPhone only |
Block third-party apps and games—the hidden setting
Once upon a time, you could just block apps and games no matter where they originated, but now it seems Microsoft has chosen to let you block individual Microsoft apps and games in your child’s family group profile.Third-party app and game permission settings are buried elsewhere. Here’s how to block third-party software:
Step 1: On the Your Family page, select the three-dot button next to your child’s name on their tile.
Step 2: Select Manage Consent on the drop-down menu (shown above).
Step 3: Select Manage this child’s access to third-party apps.
Step 4: To block third-party apps and games, select Disable Access. Return here and select Enable Access to allow your child to use third-party apps and games later.
Block unwanted installs on Windows
Just in case, make sure your child’s account listed in Windows is set to Child or Member. This setting prevents your child from making changes to Windows, rebooting into Safe Mode, and more.
The following instructions are based on Windows 11, so they may be slightly different from Windows 10.
Step 1: On the child’s PC, select the Start button, followed by the Settings icon on the Start Menu.
Step 2: Select Accounts.
Step 3: Scroll down and select Family.
Step 4: Select the child followed by Change Account Type.
Step 5: Set the account type as Child or Member if it’s not already.
Bottom line: Microsoft Family Safety is but one solution
Look, I’ve been using Microsoft Family Safety to keep my youngins in check for years, but it’s only one piece of my parental control arsenal. My family uses different platforms and different devices, so I need various tools to make sure my kids remain safe from inappropriate content and applications.
However, your approach should start at the router. I’ve tested and reviewed quite a few and compiled the ones with the best parental controls in a list (see below). I go with the free parental controls because I’m cheap, but you may find premium controls are worth the cost. Honestly, you don’t need content filtering at the router level—you really only need the ability to block devices and maybe create profile-based schedules. But if you can get some extra tools for free, the more the merrier, right?
Here are a few guides to get you started:
The second arm in your parental approach should be the operating system, and that’s where Microsoft Family Safety comes in. I’m still working on other guides for Google, Amazon, Nintendo, and PlayStation, but if you own Apple devices, here’s my guide to using parental controls across its three device types: